INTELLILINK Threat Led Penetration Testing Service
What is TLPT?
TLPT is an abbreviation for "threat led penetration test", a method of evaluating security countermeasure status by conducting simulated attacks based on attack scenarios. It has attracted attention as an advanced form of conventional security diagnosis (vulnerability assessment) and penetration testing.
The background of the current focus is the increasing level of security threats and the shift in customer needs towards penetration testing that enables visualization of the extent of damage and assessment of organizational and human resilience. In addition, in October 2018, the "Update of the Initiatives for Strengthening Cyber Security in the Financial Sector" (Press Release by the Financial Services Agency, October 19, 2018) specified "Threat Led Penetration Test" (TLPT) as a policy that financial institutions should follow, and as a result, focus on the TLPT is growing rapidly.
*Penetration Test: The inspection method that checks for vulnerabilities by attempting to penetrate server/network equipment
Advantages of conducting TLPT
By conducting the TLPT, the following issues in cyberattack countermeasures can be addressed.
Issue
Effectiveness of security measures in place is a concern
Many CISOs and executives are concerned about whether the security measures they are taking are really effective against cyberattacks.
The damage resulting from misuse of vulnerability is not clear
Since the damage and impact of vulnerabilities if they are misused cannot be anticipated, countermeasures may be postponed.
Support
Evaluate system security from the viewpoint of attacker
We verify the effectiveness of countermeasures by conducting scenario-based pseudo-attacks based on attacks that actually occur in the real world.
Clarify the damage and impact of an incident
We "Visualize" the damage at the time of an incident through simulated attacks. Based on this, the consultant will present future advice on how to strengthen cyber resilience based on the findings of consultant.
Difference between
Penetration
and Security Diagnosis
Unlike conventional security diagnostic services that determine the scope (diagnosis target) in advance, TLPT creates scenarios from the viewpoint of attacker and comprehensively assesses the possibility of intrusion and information leakage. The TLPT also aims to assess cyber resilience of organization and structure.
[Table 1] Comparison of Security Evaluation Method
| Security Diagnosis (Vulnerability Assessment) | Penetration Test | TLPT | |
|---|---|---|---|
| Execution method | Scope based | Scope based | Scenario based |
| Scope | Identification of vulnerabilities | Assessment of scope of impact of vulnerabilities | Verification of configured attack scenarios and assessment of resilience strength |
| Evaluation target | Specific server, specific system | Specific server, specific system | Entire system under customer management + organization (structure) + response process |
*Cyber resilience: Means "Ability to restore" or "flexibility". The ability and method of dealing with incident that has occurred to get the situation under control and bring it to its original state under the assumption that it is an intrusion
TLPT Service
Implementation Flow
Provision Flow
TLPT Implementation Flow
Establishment of implementation system
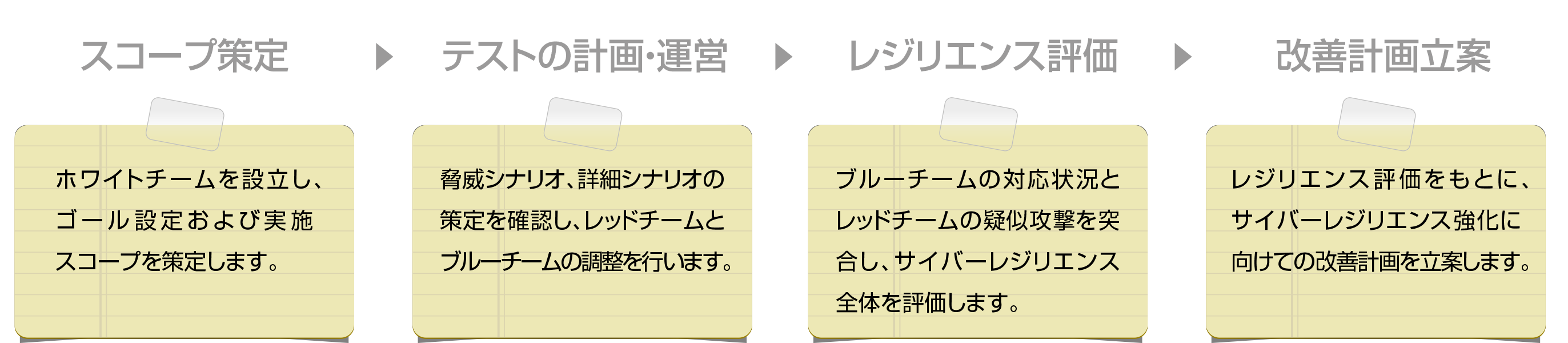
White Team Support Menu
Establish a Red Team, Blue Team, and White Team structure. (White Team Support Menu)
- Red Team (INTELLILINK): Professionals (penetration testers) familiar with hacking techniques that reproduce real cyber attacks
- Blue Team (customer): Security teams such as SOC and CSIRT that protect the organization from attacks
The White Team supervises the Red and Blue Teams and coordinates the implementation system and daily schedule. Pseudo-attacks are assumed to be carried out against the production environment. Since the objective is to evaluate the blue team, it is assumed that the scenario will not be shared with the blue team. Therefore, the white team will make a decision whether to execute the attack. Our consultants can also provide support for the white team.
Create attack scenarios
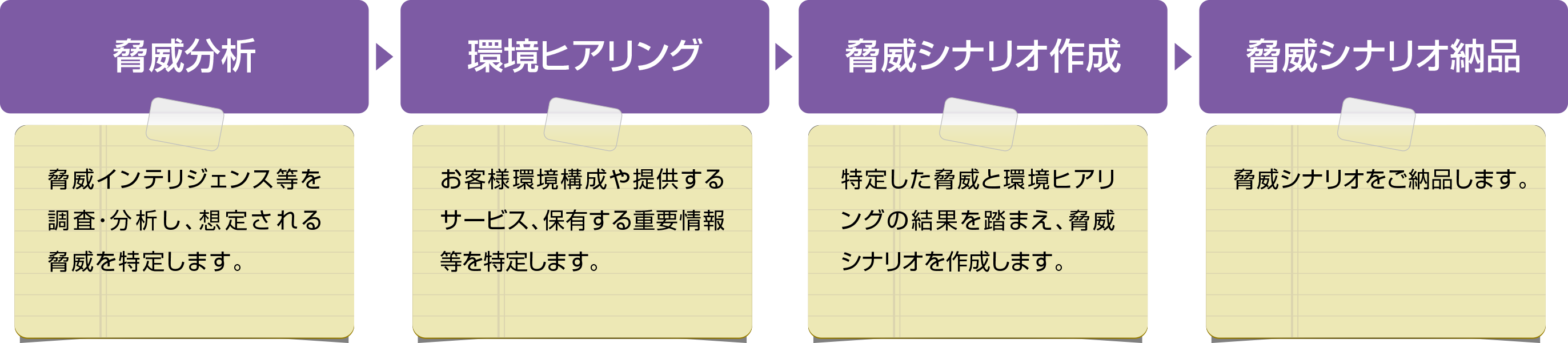
Attack Scenario Creation Support Menu
Based on interviews on the customer environment, analysis of customer risk assessment materials, and investigation and analysis of threat intelligence, attack scenarios are created for cyber attack processes that could actually occur in the customer environment. When considering attack scenarios, not only the purpose of the attack, for example, "to steal credit card numbers held by the customer", or "to steal customer/personal information held by the customer on consignment" but also the possible attackers and attack techniques that are likely to be used in the attack are analyzed and reflected. (Attack Scenario Creation Support Menu)
Prepare detailed plan
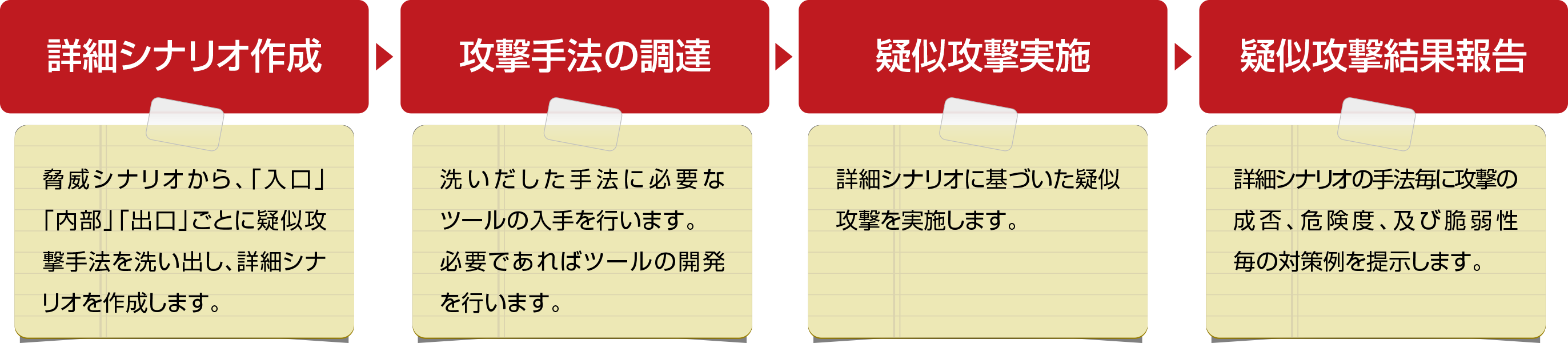
Red Team Implementation Support Menu
A specific "detailed plan" to achieve the goal is prepared. The detailed plan consists of the categories "(1) Entry Measures", "(2) Internal Measures", and "(3) Exit Measures" and a pseudo-attack plan to achieve the goal is prepared for each category. (Red Team Implementation Support Menu)
Execute pseudo attack
Red Team Implementation Support Menu
Based on the detailed plan, a simulated attack is executed on the customer's environment. (Red Team Implementation Support Menu)
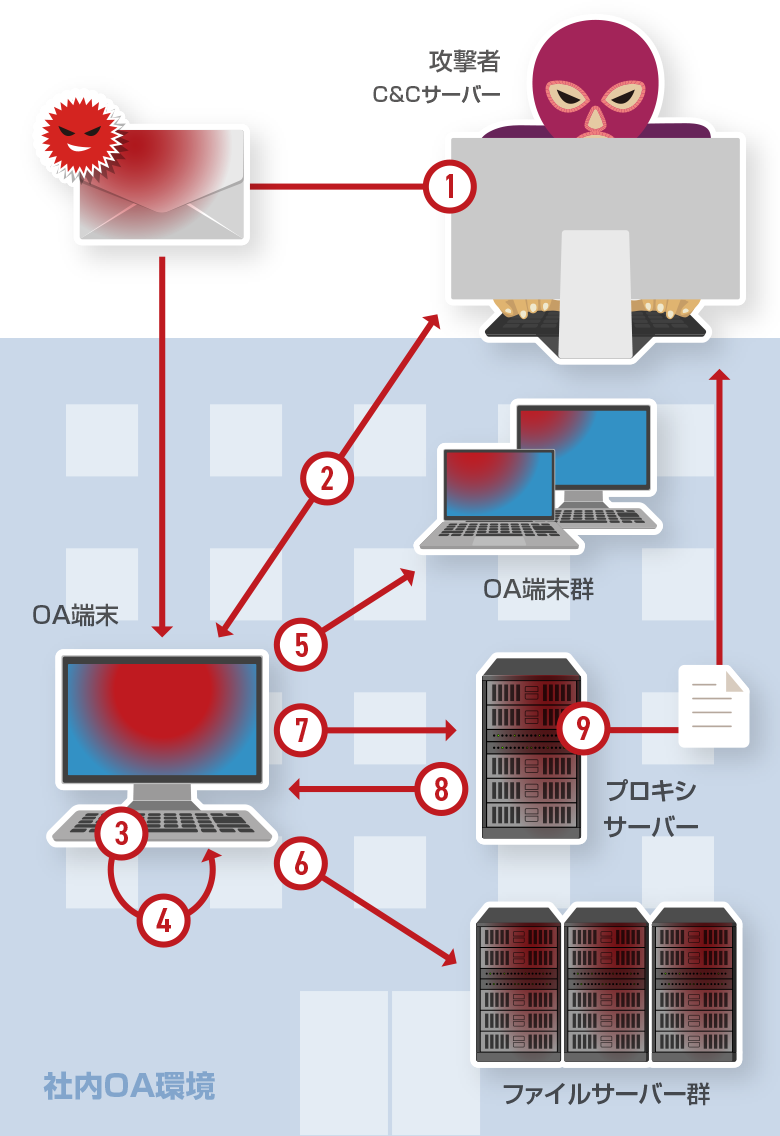
- Malware infection via email
- Malware in the OA terminal connects to the C&C server and starts external communication
- Highly dangerous vulnerabilities remain, and vulnerabilities in the OS successfully misused to elevate privileges (MS16-032) to privileged user
- The local userpassword is successfully analyzed
- A local user account is used to spread attacks to other OA terminals
- Customer information, confidential information, and otherimportant information is obtained
- Extensive damage by executing remote code (MS17-010) is caused to server
- After successful attack on server, pseudo-malware is installed and operated remotely
- By changing proxy settings information leakage channel is secured through unauthorized channels
Overall evaluation (Resilience strength evaluation)
White Team Support Menu
The white team evaluates the blue team's ability to respond to security incidents (detection, investigation, and reporting) with appropriate accuracy and duration. (White Team Support Menu)
Countermeasures Policy Advice
White Team Support Menu
Based on the findings of consultant, advice will be provided for future measures. (White Team Support Menu)
TLPT Provision Flow
We propose to provide this service as "Attack Scenario Creation Support Menu" and "Red Team Implementation Support Menu".
We will provide resilience strength assessment and "White Team Support Menu" as consulting services upon individual quotation.
Attack Scenario
Creation Support Menu



Red Team
Implementation Support Menu



White Team
Support Menu



We present the
strategy and direction of security measures utilizing
expertise of NTT DATA Group
We execute pseudo-attack to assess if the security measures implemented by the organization are functioning effectively against cyberattacks. For the simulated attacks, we collect knowledge from NTT DATA Group and actual incidents that have occurred in the real world, and create attack scenarios based on them to carry out attacks.
Based on the long-standing expertise of NTT DATA INTELLILINK in system construction and security diagnosis, consultants will conduct "threat analysis", "scenario creation", and "simulated attacks" according to the configuration of the target organization. Through the implementation of the TLPT, we can evaluate the strength of cyber resilience and propose strategies and policies for promoting security measures based on extensive solutions of NTT DATA INTELLILINK.
Related Information
* These products or services are only available in Japan.

