INTELLILINK Security Policy Formulation Support Service
Assistance in formulation of company-wide basic policies on information security
Companies and organizations need decision-making guidelines based on the nature of their business and the security risk environment to protect and utilize "information." Security policies need to be reviewed and formulated to address the risks so that the entire organization can make appropriate decisions when conducting business.
What is the Information Security Policy?
- Information assets to be protected
- Reasons for protection
- Responsibility
Information Security Policy
An information security policy clearly defines how the information and information systems are to be managed and protected.
Changes in Information Security Risk (Environment)
The scope of security management gradually changes with the changes in the information security risks and the environment. This creates risks that could not be anticipated in the execution of operations.
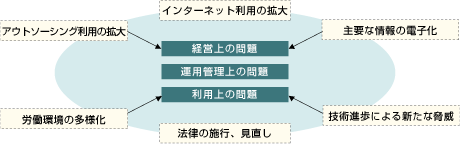
It is important that security policies be optimized to address the unexpected risks associated with the various changes in environment. The protection of information assets can be smoothly promoted in business operations by establishing security policies that address information security risks.
"INTELLILINK Security Policy Formulation Support Service" — Support from Formulation to Operation
INTELLILINK Security Policy Formulation Support Service clarifies the scope, goals, direction, and code of conduct for information security.
Through this service, we help unify the decision-making criteria across the organization by creating and reviewing decision-making guidelines according to the nature of the client's organization and business operations.
We help develop a security policy that is rooted in the organization's unique characteristics and can easily penetrate and take root in the organization.
Security Policy Review
- Process Consulting
- Assisting the customers in the process of creating security policies
- Content Consulting
- Documentation of security policy by summarizing client requirements based on interviews with clients, etc.
- Model-based
- Creating a security policy by selecting from a list of pre-defined security requirements
Security Policy Creation and Operation Flow
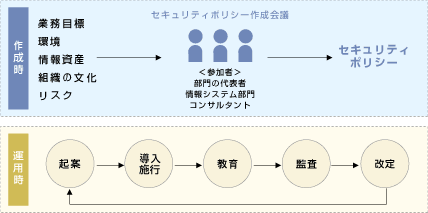
Benefits of security policy development and review
- Effective use of information and information sharing; protection of information assets from unintended use
- Establishment of an operational system to maintain and improve information security
- Presentation of standards of conduct for information security activities and clarification of responsibilities
- Clarification of procedures for responding to security breaches and other emergencies
- Awareness of security threats and risks
Flow of INTELLILINK Security Policy Formulation Support Service
| Establishment of organizational structure | Formulation of basic policy | Risk analysis | Establishment of criteria for measures | Policy creation |
|---|---|---|---|---|
| Establishment of an organizational structure to promote the project across the organization | Determining the basic direction of information security measures, including the purpose and scope of the measures | Identification of information assets, threats and vulnerabilities, and conducting risk assessment | Development of systematic criteria for measures based on the results obtained from risk analysis | Formulation of easy-to-understand policies that are rooted in the characteristics of the organization |