Website Security - DigiCert Cloud WAF
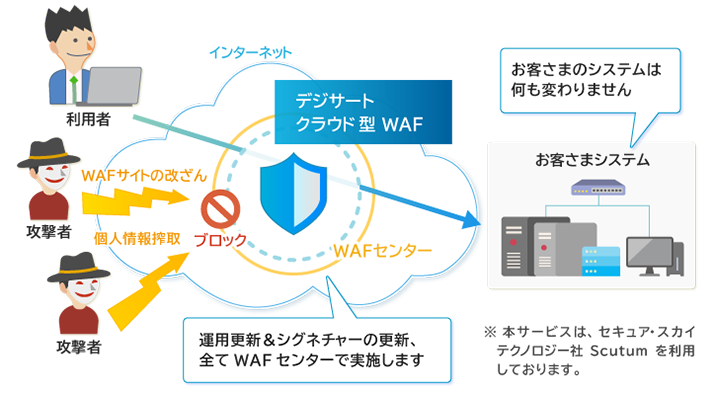
DigiCert Cloud WAF is a cloud-based service that protects against attacks targeting websites or web applications running on them. It can prevent information leakage and virus dissemination due to external attacks.
The rapid response of all systems to the security emergency patches required to keep websites secure puts a pressure on internal resources and costs. By installing a WAF (Web Application Firewall), attacks targeting vulnerabilities can be prevented and appropriate patch can be applied well in advance. In addition, vulnerabilities can be addressed without modifying websites, which leads to enhanced website security and the budget equalization.
DigiCert Cloud WAF provides WAF functions via the "WAF Center".
The WAF Center has a system in place for operation and maintenance such as adding or maintaining signatures for new attack methods, which makes it possible to install the system even without security knowledge or operational experience.
Strengths
- WAF can be installed without modifying existing system
- The only work to be done on the customer side is to change the DNS and upload the SSL certificate.
- Can be installed in a short period of time
- The WAF can be started in a short period of time because there is no need to install hardware or software.
- All operations and signature updates are handled on the cloud side
- WAF can be installed even if the customer does not have a security engineer. The WAF Center collects the latest information everyday and responds quickly to new vulnerabilities.
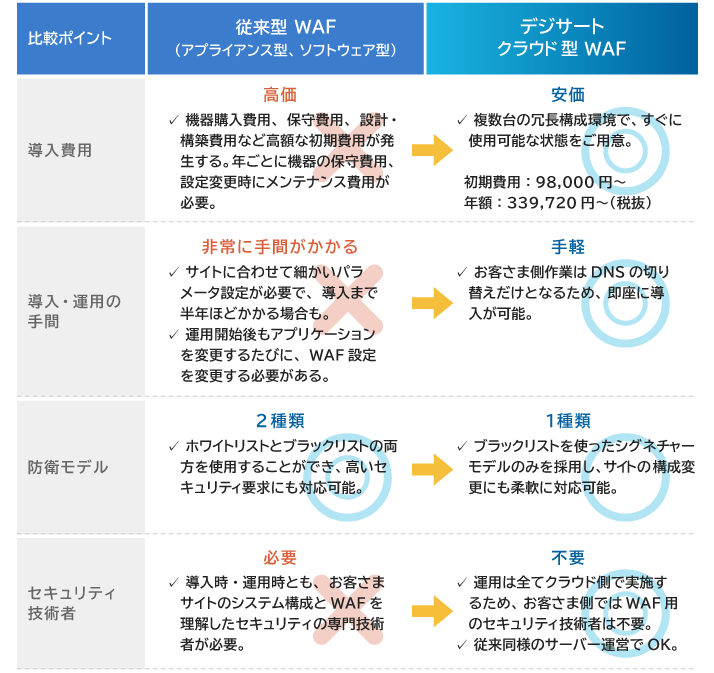
Comparison between Traditional WAF and Cloud WAF
Major Defensible Attacks
It covers many of the major attacks against web application vulnerabilities. We also update our signatures as needed to address new vulnerabilities, so the customer can maintain the latest security measures without having to be particularly aware of them.
| Attack Category | Attack Name |
|---|---|
| Authentication | Round-robin Password list attack |
| Client-side attack | Cross-site scripting Cross-site request forgery (requires adjustment at the time of installation. There might be a separate charge for this service depending on the adjustment.) |
| Execution by command | Buffer overflow OS command injection SQL injection Xpath injection Format string attack LDAP injection SSI injection |
| Information disclosure | Directory indexing Information leakage Past traversal Locating resources |
| Attack targeting specific middle-ware/framework | Attack using vulnerabilities in Apache Struts 1&2 Attack using vulnerabilities in GNU bash (CVE-2014-6271) Attack using SSL 3.0 vulnerability (CVE-2014-3566) REST API Vulnerability in WordPress 4.7.1 |
| Anti-malware | Drive-by download (email spread by gamblers) attack |
| Attack on the platform | DoS attacks exploiting platform vulnerabilities (such as ApacheKiller, hashDoS) DoS attack from a small number of IP addresses (such as mass normal communication, Slowloris, SYN flood attack) |
List of Key Functions
| Defense function | Blocks the communication if a pre-registered unauthorized communication pattern is detected |
|---|---|
| Monitoring function | Records the communication when a pre-registered illegal communication pattern is detected (does not block the communication itself) |
| Log function | Records the communication that appears to be fraudulent and makes the log accessible |
| Software update function | Updates software to improve defense function |
| Signature update function | Updates unauthorized communication patterns from time to time to improve effectiveness of protection |
| Specific URL exclusion function | Excludes web pages that do not require defense function from protection |
| Report function | Reports the following information on the management screen (using a Web browser) • Statistical functions (attack source, attack type, action) • Top tally of attack sources, types of attack |
| IP address rejection/authorization function | Rejects communication from a specific IP address or allows communication only from a specific IP address |
| SSL communication function | Decrypts and protects encrypted communication |
Flow from Installation to Operation
The only work to be performed on the customer side is the part in red below.
| Advance preparation | Start service | Monitoring period | Start service | Start service |
|---|---|---|---|---|
| • Fill out the hearing sheet and place order • Acquisition/configuration of certificates for WAF |
• Change DNS settings • Launch service in the form of monitoring attacks without defending against them |
• Monitor WAF settings for about one month and confirm that normal communication does not stop | • Start defense | • Troubleshooting: 24 hours a day and 365 days a year • Product support: Weekdays 9:30-17:30 |