INTELLILINK Database Security Assessment Service for Oracle
Vulnerability visualization solution, a first step toward prevention of targeted database
Databases store many important information assets such as personal information, technical information, and intellectual property. In many cases, companies have suffered unexpected damage due to data breach or data falsification that steal information to get cash. It could lead to situations that cannot be ignored such as a loss of customers due to a damaged brand image, countermeasures or compensation costs, and administrative guidance that could affect the performance and survival of the company.
When considering database security measures, the first thing to do is to understand the current situation. INTELLILINK Database Security Assessment Service for Oracle can diagnose hidden vulnerabilities in Oracle databases on-premises or in the cloud in a short time and at low cost. We will present you with diagnostic results based on security settings recommended by Oracle and show you the points that need to be addressed. The diagnostic report classifies security risks into six levels in ten diagnostic areas, providing visualization of database configuration, operational, and implementation risks. We support customers who "want to diagnose the security level of their databases" or "need a security check by a third party to undergo a security audit".
Importance of database security, which has to be strong
The database runs on a strictly secured server data center that is inaccessible to the public. It was thought to be safe in the past because it runs on an internal network isolated from external networks and there is no fear of direct database access. However, the means of attack has become more diverse and sophisticated in recent years, and there have been incidents of information leaks via application server from the databases that cannot be directly accessed.
While it is very important to have strong security measures in place for the network and applications and ensure boundary protection, this does not mean that the database should be left unprotected. The malicious insider can easily steal the data if unprotected database can be accessed directly. It is necessary to consider how to manage the important data to be protected, control and manage the users who have access to the data, and review security holes in the database.
Various guidelines for strengthening database security
With the implementation of the My Number Act, the amendment of the Act on the Protection of Personal Information, and the addition of description to the security guidelines issued by the National Center of Incident Readiness and Strategy for Cybersecurity. (NICS), database security measures are becoming even more demanding.
| Name | Activities for Strengthening Security | Target | |
|---|---|---|---|
| PCIDSS(*1) | December 2004 | Establishment of PCI DSS | Companies that handle credit cards |
| November 2013 | Upgraded to v3.0 Added encryption, access control, auditing, masking, configuration management// |
||
| Cyber Security Management Guidelines(*2) | December 2015 | Published guidelines Added multi-layered protection and advanced encryption, access control, and auditing of critical data (databases, files)// |
Company managers Companies that provide IT systems and companies for which using IT is essential for management strategy |
| November 2017 | Added description requiring the establishment of mechanism for attack detection and recovery// | ||
| Common Standards for Information Security Measures for Government Agencies(*3) | September 2005 | Published Common Standards for Information Security Measures for Government Agencies | Government agencies |
| August 2016 | Published 2016 version Added new database items. Added split administrative privileges, access control, auditing/detection and encryption// |
Public offices, independent administrative institutions | |
| Revised Act on the Protection of Personal Information(*4) | September 2015 | Law passed and promulgated | Business operators or industry associations that hold personal information |
| November 2016 | Published guidelines Clarified personal information to be protected AddedAccess control, encryption, auditing and detection, cipher processingin the General Rules |
||
| Revised Installment Sales Act(*5) | February 2017 | Law passed and promulgated Added description demanding PCIDSS compliance when credit card information is retained. | Companies that handle credit cards |
- *1: https://www.pcisecuritystandards.org/
- *2: https://www.meti.go.jp/policy/netsecurity/mng_guide.html
- *3: https://www.nisc.go.jp/active/general/kijun30.html
- *4: https://www.ppc.go.jp/personalinfo/
- *5: https://www.meti.go.jp/policy/economy/consumer/credit/112kappuhanbaihoukankeishiryou.html
First step in strengthening database security
The first step in considering database security measures is to understand whether the current configuration has any vulnerabilities. Due to the emphasis on operational efficiency, the assignment of strong privileges to general users, and the lack of internal resources, user inventories are not kept for a long period of time and temporarily created test users or accounts of employees who have left the company are left neglected. In addition, the robustness of database will reduce with the cases left neglected where necessary security patches are not applied due to failure to catch up with patch information released by vendors.
It is important to diagnose database vulnerabilities and visualize areas that need to be addressed and items that need to be strengthened further. This is not just a one-time diagnostic service, but also supports periodic diagnostics, which can be useful for early detection of newly emerging risks.
Low-cost and quick security diagnostics of Oracle database
| Service Overview |
|
|---|---|
| Price |
One-time300,000 yen ~ *Price for one database regardless of RAC configuration. Please discuss if the number of instances in RAC configuration exceeds 4 *If you wish to have periodic diagnosis, please discuss separately. |
| Period | About 5 business days after running and returning the diagnostic script results and configuration file//// |
Scope of service
Supports a wide range of DB versions
Oracle Database 10gR2 or later
(10.2.0.4 or later)
Supports various OS types
Linux, Solaris, HP-UX,AIX, Windows
Also support cloud environment
On-premises, cloud
(such as Oracle Cloud, AWS (excluding RDS))
*The information collection script used in this service must be executable in the environment where the DB is running.
Diagnosis report
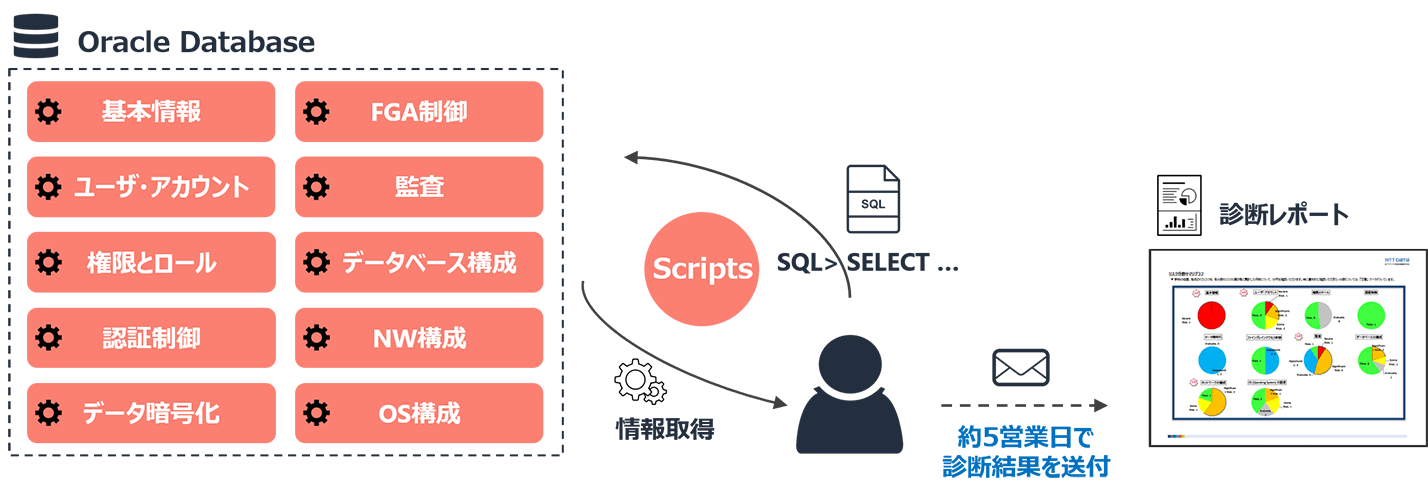
For each of the 10 diagnostic areas, we determine the gap with Oracle recommended configuration (value). We report the gaps by classifying them into six risk levels in accordance with the judgment criteria of Oracle. From this report, you can easily visualize and check the points of security risks.
10 diagnostic areas
| # | Diagnostic Area | Overview of Diagnostic Items |
|---|---|---|
| 1 | Basic information | Usage of security patches and security features |
| 2 | User account | Default table area, password related, profile settings |
| 3 | Permissions and roles | Strong administrative privileges, strong roles |
| 4 | Authentication control | Behavior control of privilege management user |
| 5 | Data encryption | Transparent data encryption |
| 6 | FGA control | Access control implementation |
| 7 | Audit | Audit trail setting, audit policy |
| 8 | Database configuration | Initialization parameters, dictionary access rights |
| 9 | NW configuration | Network encryption, client connection control |
| 10 | OS configuration | OS authentication, directory permissions |
Risk Summary Graph
The risks found as a result of the diagnosis are classified into six levels, and the number of occurrences is tabulated. The number of risks that occurred in each diagnostic area is shown in the "Risk Area Summary Graph".
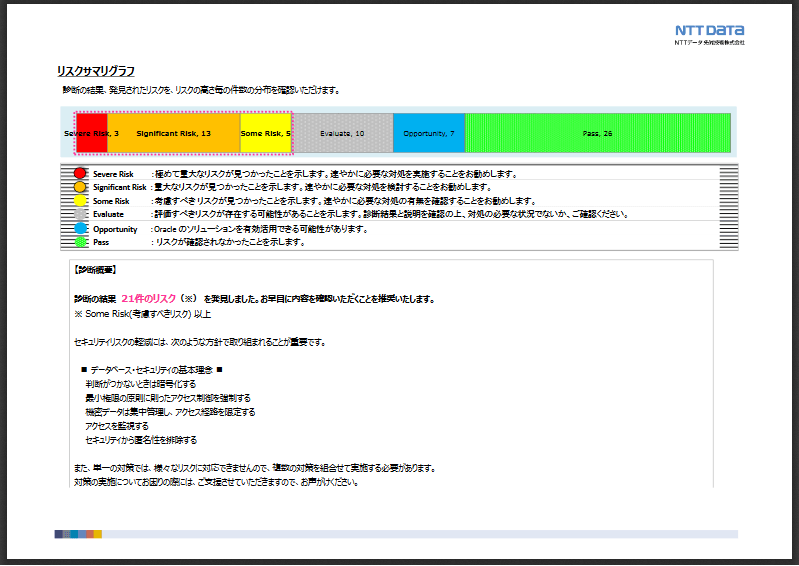
Risk Area Summary Graph
Risks found in each of the 10 diagnostic areas are classified into six levels and the number of occurrences is tabulated. Areas that need to be checked on priority are marked with a "Caution" mark.
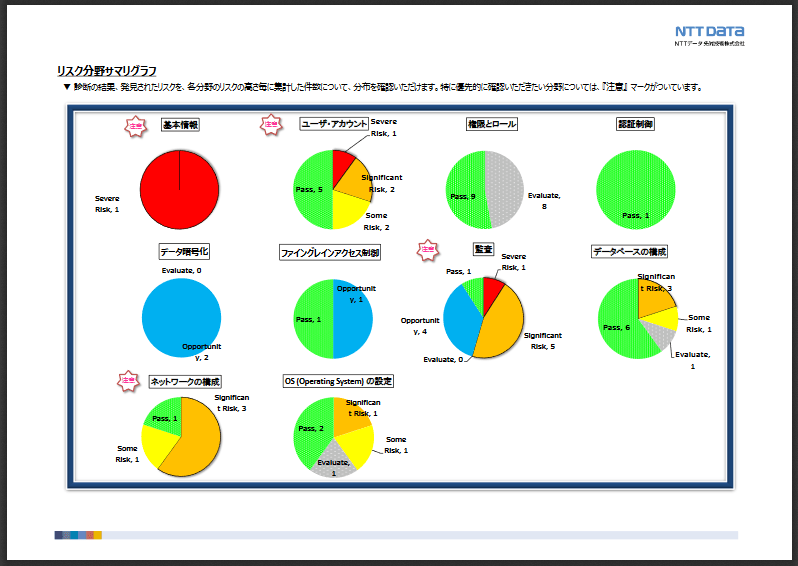
*The image above shows a part of the diagnostic report. The actual report provides a more detailed description of each risk.
Prerequisites for service
| Please consult us for implementation of measures to address vulnerabilities |
We provide support for the study and implementation of security risk countermeasures for a separate fee. (If you have an Oracle maintenance contract with us, QA will be handled by Oracle maintenance.) *We visualize and report security risks, but visualization of all security risks is not guaranteed. |
|---|---|
| Please run the information collection script at your convenience. | Customer needs to execute the scripts we provide. |
| We do not access the business data |
We search (SELECT) parameter and dictionary information from the Oracle database and export it to the output file. *Performance impact on script execution is negligible. |
Service Flow
-

1. Hold a meeting and collect information
We will collect information about database configuration, environment information, version, etc.
-
2. Provide diagnostic materials
We will give you information collection script to be used in the diagnosis.
-

3. Run information collection script
The customer runs the script in the database to be diagnosed.
-

4. Return results after running the script
You will be asked to provide listener.ora and sqlnet.ora along with the information you have collected.
-

5. Analytical investigation
We will analyze the data in about 5 business days after we receive it.
-

6. Send diagnostic report
We will send the diagnostic report to customer.
Contact
When considering database security measures, the first thing to do is to understand the current situation. Why don't you visualize hidden risks with a security diagnosis? Please feel free to contact us.