INTELLILINK Cyber Incident Response Exercise Service
Current status of security incident exercising
No matter how prepared you are for increasingly sophisticated cyber attacks, security incidents can still occur.
Under such circumstances, it is necessary to establish, maintain, and improve a system based on the assumption that security incidents will occur.
Recently, exercises simulating security incidents for checking and strengthening the organization's capabilities and responsiveness have been gaining importance.
Ministries and agencies, security organizations, and CSIRTs*1are increasingly conducting exercises for companies and organizations.
The Financial Services Agency (FSA) has launched the "Financial Industry-Wide Cybersecurity Exercise (commonly known as Delta Wall)"*2 to enhance the level of cyber security measures in the entire financial industry*2.
The National center of Incident readiness and Strategy for Cybersecurity (NISC) also conducts cross-disciplinary exercises on an ongoing basis.
It is important for each company and organization to set up suitable scenarios and conduct appropriate exercises.
- *1 CSIRT: Computer Security Incident Response Team A generic term for a team of professionals that handles computer security incidents. In general, in addition to incident handling, CSIRT also performs tasks such as collection and analysis of incident-related information, vulnerability information and predictive attack information as well as the development of response policies and procedures.
- *2 "Financial Industry-Wide Cybersecurity Exercise" :https://www.fsa.go.jp/news/28/sonota/20161020-1.html
Why are Cyber Incident Response Exercises Conducted?
These exercises provide training on understanding the content related to cyber incident response and practicing it appropriately.
- Review the overall scenario of cyber risk in your company or organization
- Understand the means to monitor within a company or organization's network and detect cyber-attack activity.
- Improve cyber incident response and defense capabilities by utilizing threat information obtained through information sharing with external organizations/agencies.
Overview of INTELLILINK Cyber Incident Response Exercise Service
Service Overview
This service is designed to provide participants with the experience of responding to cyber incidents to understand the methods and procedures for responding to security threats, and to identify issues and gaps in current policies, procedures, and systems.
Based on scenarios simulating actual cyber incidents, participants can learn how to respond to security incidents brought about by cyber incidents, including detection of intrusions and attack activities, and notification and reporting to management and external stakeholders.
Service Structure
Exercises include "tabletop exercises" for decision makers and "simulated technical exercises" for the actual personnel performing operations, such as CSIRT personnel.
- Tabletop exercises
- Discussions among decision makers from IT, planning, risk management, business operations and public relations departments, including senior management. For management
- Simulated technical exercises
- Practical training in responding to cyber incidents using a simulated corporate network environment. For actual personnel performing the operations
Cyber Incident Response Exercise [Tabletop Exercise Service]
Overview of Tabletop Exercise Service
Our facilitator (member of our organizing team) provides "incident situations (scenarios)" to the players (client participants), based on which the players discuss the possible impact of an attack on their organization and the methods of handling the same.
- Time required: 3 to 3.5 hours
- Participants of tabletop exercises: Member of the management and decision makers from all departments involved in incident response (IT, planning, risk management, business operations, public relations, etc.)
1. Conducting discussions: Discussing the risks associated with a cyber incident and the appropriate response by the company
- Information assets targeted by attackers
- How attackers gain a foothold in the company (intrusion technique)
- Policies and procedures for protection and response
- Risk of being attacked
- Cost of incident response (time, resources, lost productivity)
- Long-term risks (brand, reputation, competitive advantage, intellectual property)
- External responses in the event of an attack (with respect to customers, shareholders, government/police), etc.
2. Clarification of issues
Identify issues in the existing cyber (information security) incident response system, communication and coordination and recovery procedures.
Image of Tabletop Exercise
Effectiveness of Tabletop Training Service
Through exercises based on scenarios simulating actual cyber incidents, we can create awareness regarding the current situation and clarify the issues.
- Verification of the responsiveness capabilities of the organization
- Clarification of gaps in understanding and perception among the members of the incident response team
- Identifying the business impact of cyber incidents
- Finding ways to strengthen and improve defense capabilities
- Clarification of the gap between regulations and the current situation
Flow of Tabletop Training Service
We provide assistance in implementing exercises tailored to the client's business environment.
| Hold a meeting and collect information | Scenario-based review |
Exercises | |
|---|---|---|---|
| Upon receiving a request for conducting training, we hold a meeting to collect the necessary information. We ask about the structure of the client's organization in order to create exercises based on scenarios as close to the reality as possible. Based on the information collected from this meeting, we prepare preliminary scenarios. | We present exercise scenarios as a starting point. Comments received from the clients are reflected in the scenarios. | Training can be conducted in as little as one month after receiving a request. We conduct exercises and review based on the presented scenarios. The duration of the exercise is 3 to 3.5 hours. | |
 |
|||
| Minimum 1 month | |||
Cyber Incident Response Exercise [Simulated Technical Exercise Service]
Overview of Simulated Technical Exercise Service
Practical training on how to respond to cyber incidents using a simulated corporate network environment in a virtual environment.
- Time required: 7 to 8 hours
- Participants of technical exercises: System administrators, network administrators, help desk personnel, etc.
- 3-6 persons per team; maximum 2 teams
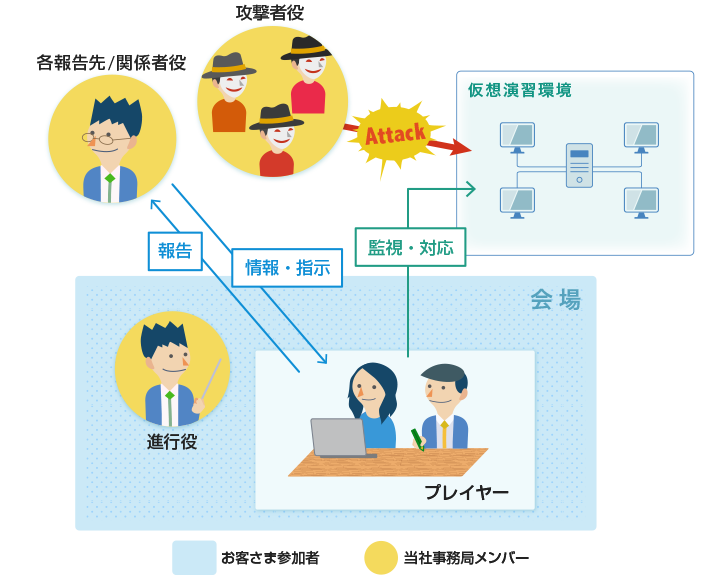
1. The players act as security team members of a fictitious company to detect and respond to cyber incidents launched by attackers, report to the relevant reporting parties, and take defensive measures against cyber incidents
- Detection: Upon detection of an incident or upon receiving information and instructions from each relevant reporting party, the team discusses a response policy and takes action
- Discussion: Team discusses response policy
- Practice: Team investigates, reports and directs as appropriate, and implements defensive measures
2. Review
- Conducted immediately after the end of the exercise
- Feedback and summary of exercises
- Explanation of the incident (description of the purpose of the attack and the attack methods used)
- Observations of responsiveness shown by players
3. Submission of report
- Submitted approximately two weeks after the exercise is conducted
- Report contains the analysis results of how players responded to the exercise, the extent to which the objectives of the exercise were achieved, and what issues were identified
- Compilation of findings and proposed measures for improvement in response to cyber incidents
Image of Simulated Technical Exercise
Effectiveness of Simulated Technical Exercise Service
Simulating the process of response to cyber incidents helps in identification of issues, which further helps in strengthening countermeasures to cyber incidents.
- Response capabilities and procedures can be verified
- Are the current response procedures capable of handling the incident?
- Are the line of instructions and information sharing appropriate?
- Can help bridge gaps in perception and understanding among members of the security team
- Helps individual members understand the whole picture beyond the scope of their work
- Elevates the level of experience of each member of the team
- Helps recognize gaps in current security measures
- Appropriate log management
- Proactive information sharing with external parties
Flow of Simulated Technical Exercise Service
We provide assistance in implementing exercises tailored to the client's business environment.
| Hold a meeting and collect information | Scenario-based review | Exercises | Report submission |
|---|---|---|---|
| Upon receiving a request for conducting training, we hold a meeting to collect the necessary information. We ask about the structure of the client's organization in order to create exercises based on scenarios as close to the reality as possible. Based on the information collected from this meeting, we prepare preliminary scenarios. | We present exercise scenarios as a starting point. Comments received from the clients are reflected in the scenarios. | We conduct exercises and review based on the presented scenarios. | Based on the results of the exercise, we present a report with observations regarding the level of achievement and challenges. |