Threat Intelligence Platform (TIP) "EclecticIQ Platform"
Security setups such as a CSIRT*1are handling an exponential increase in the type and volume of information, such as open-source threat information, threat information collected by security vendors, threat information detected by security equipment, threat information shared among organizations and vulnerability information in products. There has been a dramatic rise in the need for integrated analysis of such threat information from external sources and threat information investigated/detected by the organization itself.
In response to this need, large organizations are introducing and using "Threat Intelligence Platforms (TIPs)" that collect, analyze, and share a wide variety and large volume of threat information.
What is TIP?
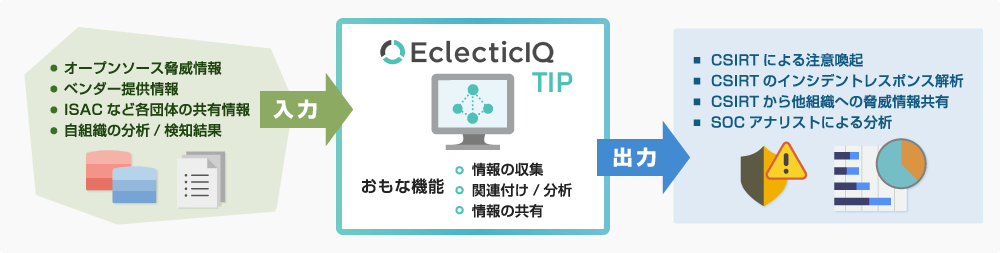
The "Threat Intelligence Platform (TIP)" provides an infrastructure to the SOC, CSIRT, or ISAC*2(that unites such organizations) for collecting, analyzing, and sharing cyber threat information.
Installation Effect
- Enables more efficient and automated threat intelligence collection and threat intelligence distribution sharing among collaborating organizations.
- Improves the efficiency of alerts sent by CSIRTs and other organizations.
- Enables analysts conducting the analysis to make the best decisions based on the characteristics of the attack.
- Allows aggregation and analysis of threat information from different sources and formats.
- Threat information correlation and analysis capabilities of TIP make it possible to conduct analysis considering multiple pieces of information horizontally.
(Figure) TIP
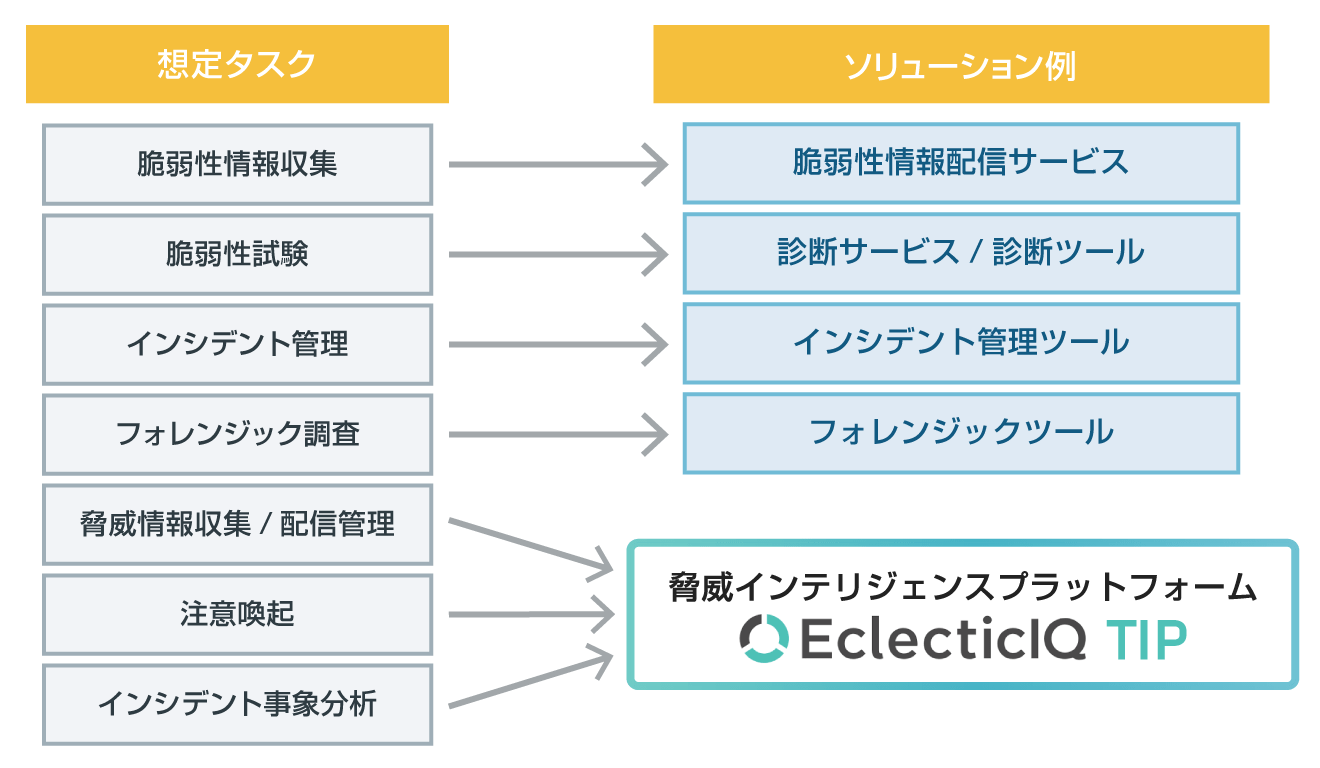
TIP in CSIRT operations
CSIRT can use TIP as a solution to assist in the following tasks.
Examples of Tasks Handled by CSIRT
Key Functions of EclecticIQ Platform
- Gathering threat intelligence
- Capable of capturing threat intelligence in a variety of formats.
Can collect structured as well as unstructured data. - Analysis assistance to analysts
- TIP offers collaboration functions including team workflows, analysis support functions such as graph output, pivot tool, add/delete classification (tags), and report generation functions. This allows analysts to decipher large amounts of data and quickly identify attack trends and relationships, understand IOCs*3, etc.
- Registration and sharing of threat intelligence
- Results of analysis conducted by your organization can also be registered as part of the threat intelligence. In addition to output of reports for reading by analysts and managers, reports can also be output in a format that can be imported by security and network devices.
- Supports standard protocols
- Supports STIX/TAXII (protocols for sharing of threat information) for sharing with the broader community. Also supports various other input/output formats.
- Supports on-premises/cloud-based environments
- TIP can be set up and used in both on-premises and cloud-based environments.
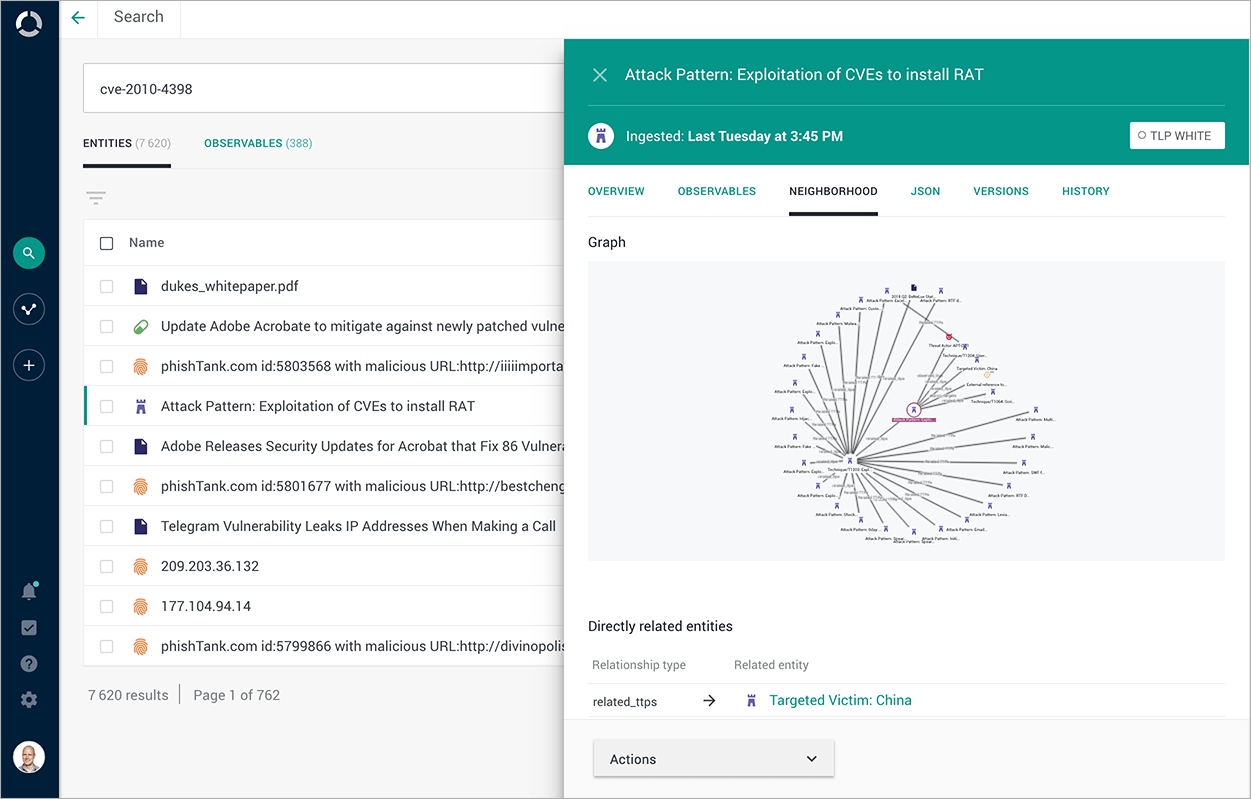
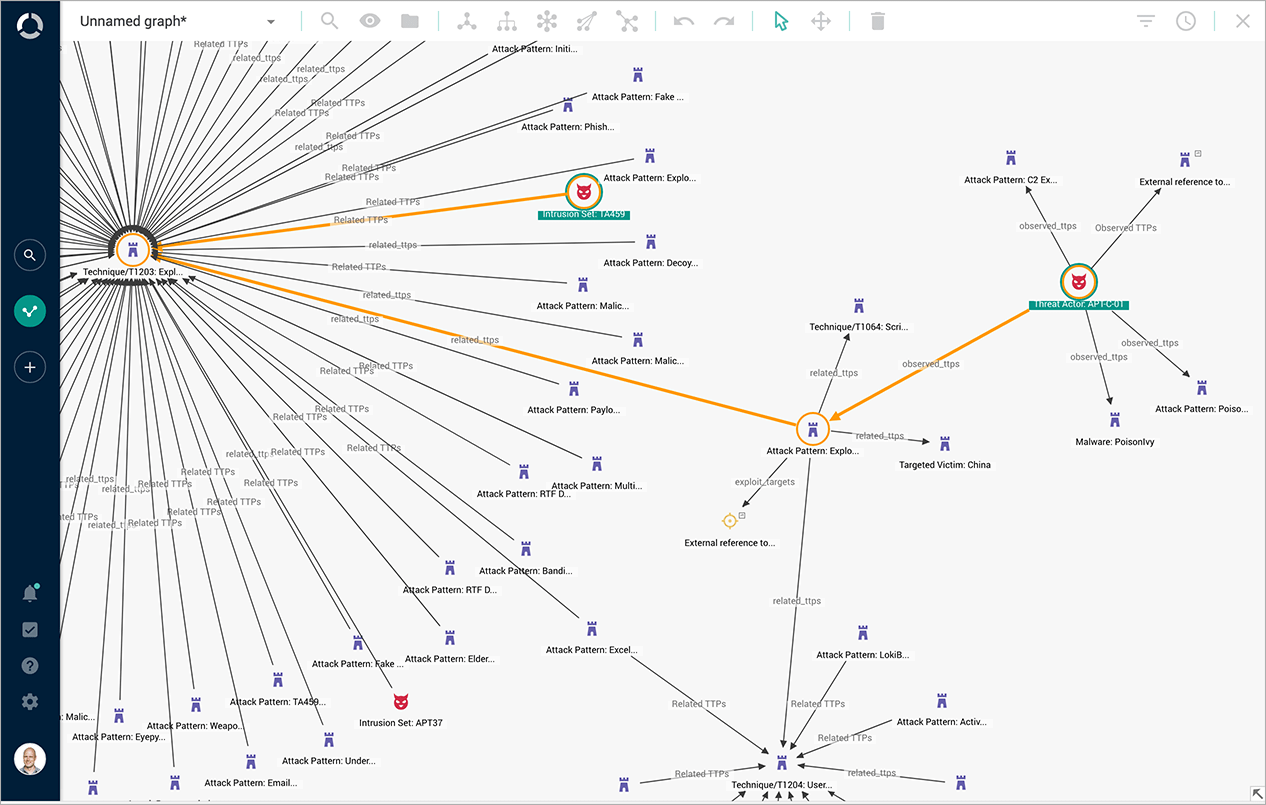
Example of Analysis Screen
Search keywords display a series of information such as attack campaigns and the activities of the attackers (actors).
Example of analysis screen: Search results in context
Example of Analysis Screen
Threat information from different sources is combined to establish correlations such as between attackers (actors) and communication pathways.
Example of analysis screen: Display of correlations
Features of EclecticIQ Platform
- The manufacturer, EclecticIQ, is a key member of the organization responsible for developing STIX/TAXII (protocol for sharing threat information).
- It is equipped with various means of collaboration such as STIX/TAXII (protocol for sharing threat information).
- and a variety of analysis and analysis support functions.
- Results of analysis by analysts can also be registered as threat information and merged with externally imported threat information.
- Extendable with your own API or SDK.
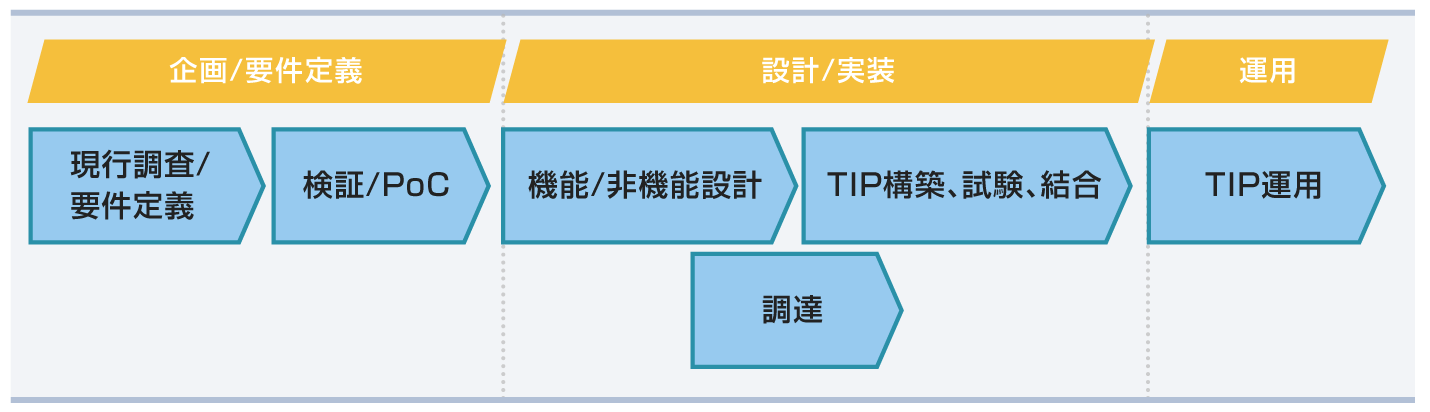
Implementation Flow (TIP Implementation Support Service)
[1] Planning/Requirements defining phase
- We identify the scope of work of the organization.
- As part of the survey, we identify the information collected by the organization, and sort the status of utilization and issues.
- As part of establishment of requirements, we organize the threat information that needs to be collected by the organization and the use cases of the collected information.
- We offer PoC (Proof of Concept) service to support the feasibility studies for expected functional/non-functional requirements.
[2] Design/Implementation phase
- We support functional/non-functional design of stand-alone platform as well the platform to which products are expected to be linked.
- We assist in building/testing the stand-alone EclecticIQ Platform and in testing the products to be linked.
- The EclecticIQ Platform is delivered along with the accompanying software and hardware.
[3] Application phase
- We provide support and training via the manufacturer.
- We plan to develop our own help desk and operational support in the future.
Strengths of NTT DATA INTELLILINK
We have accumulated expertise from assisting customers to consider TIP implementation, participating in TIP demonstration experiments at various security organizations, and experience in incident response.
Our strength lies in our ability to leverage this experience to provide TIP implementation support for effective threat intelligence utilization and efficient analysis support. In addition, we can also provide business design support for securing and handling information sources using the knowledge of our incident response staff, who are also activeas a CSIRT.
- *1: "CSIRT (Computer Security Incident Response Team)" refers to a team that responds to computer-related security incidents and handles a variety of tasks both during routine activities and when incidents occur.
- *2: "ISAC" stands for Information Sharing and Analysis Center. ISACs are set up with the aim of sharing information about cybersecurity within the same industry to improve defense capabilities.
- *3: "IOC" stands for Indicator of Compromise. Refers to pieces of information indicating that an attack has been made.
Official website of EclecticIQ
Official website of EclecticIQ