What is "Cybereason EDR"?
Cybereason EDR constantly monitors if any suspicious person is engaged in malicious activities in the customer network environment, conducts correlation analysis of the information using an AI engine on the cloud, and detects cyber attacks in real time. Once the attack is detected, Cybereason EDR promptly sends the details of the attack on the management screen where they can be viewed in an easy-to-understand manner.
It provides a cybersecurity platform that can instantly visualize the full picture of an attack to respond to the attack quickly.

Why EDR became necessary?
Telework is becoming popular due to the diversification of work styles, but terminals that do not pass through the internal security gateway of the company have lost their security "shield" at once, leaving them unprotected.
In addition, with the promotion of DX through operational efficiency, applications and data are increasingly migrating to the cloud, and access to the cloud from a telework environment does not pass through the internal security gateway.
In addition, attacks are becoming more sophisticated and difficult to deal with using conventional solutions, making new security measures essential.
The idea to eliminate those security risks is the Zero Trust Model (Zero Trust Network). The zero trust model is based on the idea of preventing threats to information assets by not trusting and verifying all access to the data to be protected.
It is necessary to further strengthen the security of each endpoint, and terminals such as PC, mobile, and application servers where data to be protected from attacks is stored.
In addition, "Common Standards for Information Security Measures for Government Agencies (FY2021)"(*1) includes description about EDR and MSS as examples of measures to prevent the spread of malware via network, and encourages consideration of outsourcing the managed security services in operations.
*1 Key Points of the Revision of "Common Standards for Information Security Measures for Government Agencies"
https://www.nisc.go.jp/pdf/policy/general/rev_pointr3.pdf
Challenges in Conventional Solution
- The network boundary defense approach focuses on initial infection, and it is difficult to detect and address attack activity after penetration.
- Terminal management becomes complex and it is difficult to prevent threats.
Solution
- Automated terminal management
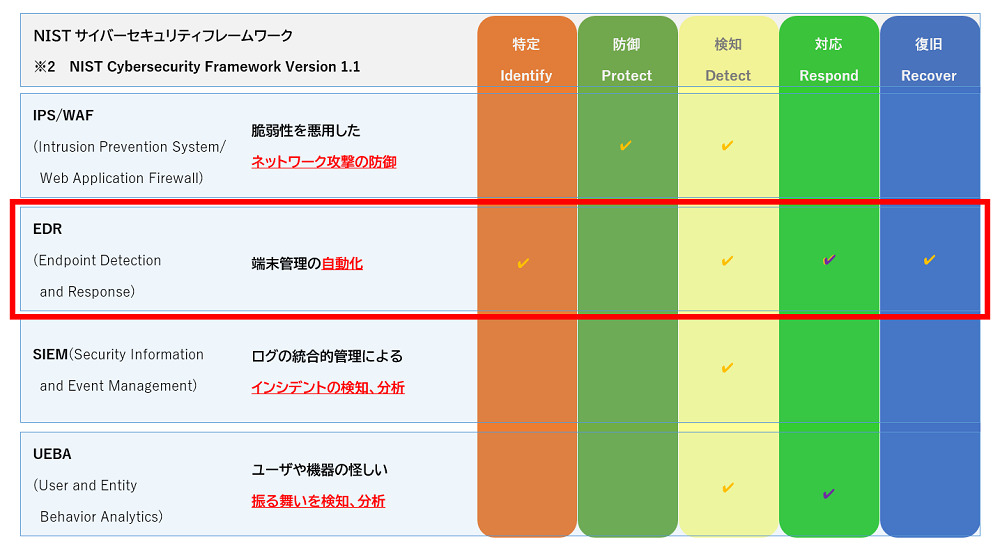
|
*2 NIST Cybersecurity Framework Version 1.1 document link |
Cybereason Features
(1) Promptly identifies the entire attack
- When suspicious behavior is detected, Cybereason can immediately identify the status of infection to other endpoints. This allows for smooth initial response to incidents, including accurate assessment of the situation, measures to control the spread of damage, and identification of the cause of the incident.
- Correlation analysis using machine learning enables detection of sophisticated attacks and internal frauds that are difficult to detect using existing products.
(2) Remotely handles multiple attacked terminals at once
- Cybereason can remotely quarantine affected terminals, stop the processes, quarantine the files, and delete the registry deletion all at once. In incidents where speed of response is important, damage can be minimized by investigating and responding to multiple terminals at once that have been subjected to the same attack.
③ Easy installation, lightweight operation
- Cybereason sensors running on endpoints are designed to minimize the load on endpoints. In addition, NGAV, which prevents malware infiltration before it occurs, and EDR, which detects suspicious activity after an infiltration and responds quickly, are provided as a single sensor for efficient management of attacks.
- Timelines for each user are automatically created, which enables quick post-detection analysis and response.
- The innovative sensor technology of Cybereason is optimized to prevent impact on the business applications or operating systems.
④ Reliable support system, such as easy-to-understand, visualized management screen in Japanese
- The Cybereason management screen displays the results of the automated analysis graphically in chronological order in Japanese, so that the entire picture of the incident can be quickly grasped.
- Report can be generated in Japanese
- Monitoring, analysis, and various support by our Japanese subsidiary
- Monitoring/analysis/reporting by security experts through MDR service (option to monitor detection alerts, option to act as control agent)
Cybereason Installation Image
The dashboard provides an intuitive visualization of attacks in progress within the organization, and enables users to visualize and extract the summary of the details of the incident analysis results and take immediate action remotely with a single click. It also has a smooth investigation function that efficiently manages response status and assists analyst operations, and enables identification of problems in real time.
And since Japanese reports can be generated automatically with a single click of a button, they can be effectively used for reporting work when incident occurs.
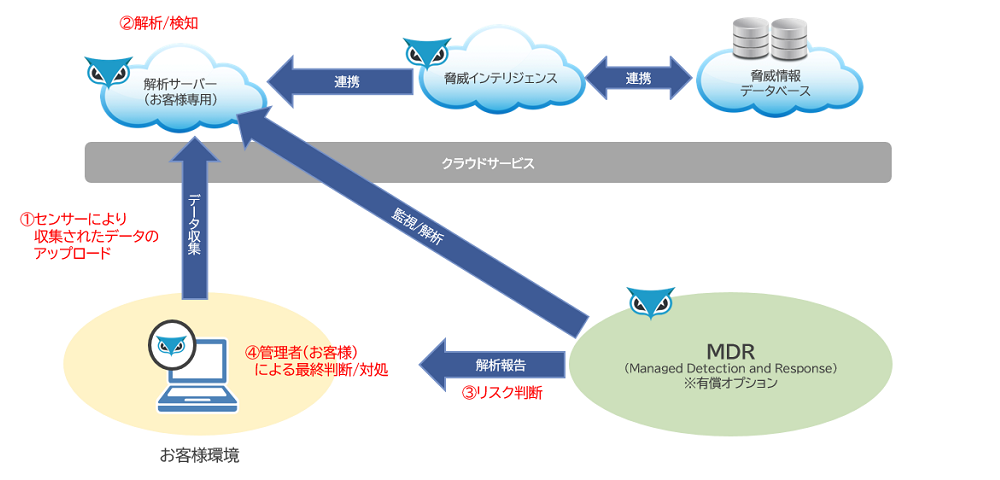
Cybereason Installation Flow
We provide one-stop services from design and construction to implementation, maintenance, tuning, and monitoring operations.
Hold a meeting and collect information
Construction
Operation
* These products or services are only available in Japan.