Unauthorized Access Monitoring Service (IDS)
Quick detection and notification of unauthorized access that cannot be prevented by firewalls alone
In order to prevent unauthorized network intrusions and maintain security, it is necessary to have a system that can identify any signs of unauthorized access in real time while plugging known security holes.
Unauthorized access monitoring service (IDS) supports the maintenance of a secure system environment by monitoring unauthorized access and equipment status 24 hours a day, 365 days a year at our monitoring center.
Challenges in combating unauthorized access
Although security products such as firewalls are generally installed to prevent unauthorized access, is that really enough to provide peace of mind?
Purpose of Firewall
Detect and block unauthorized communications by monitoring data flowing over the network.
Operational issues
- Access to permitted ports sometimes even allows attacks to pass through.
- It is operationally difficult for the administrator to constantly check the logs to determine where an unauthorized access is occurring, and it is also difficult to take immediate action.
Purpose of IDS
Constantly check communications over the network on behalf of the administrator. Quickly detect unauthorized access that could not be prevented by a firewall and notify the administrator about the same.
Operational issues
- Merely installing the system does not prepare your environment for anything.
- Signatures need to be tuned.
- Many false positives are difficult to determine from IDS device alarms alone.
Features of Unauthorized Access Monitoring Service
Unauthorized access monitoring service (IDS) collects latest security information and performs monitoring 24 hours a day, 365 days a year to check for unauthorized access that cannot be protected by firewalls.
This reduces the burden of system operation on our clients by making accurate judgments in response to unforeseen situations.
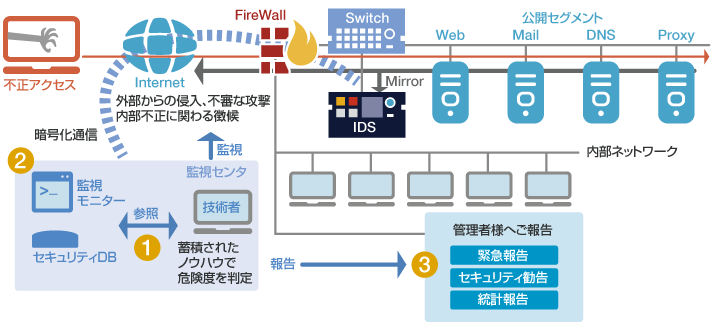
- 1. Unauthorized access detection and determination by IDS
- Based on the client's environmental information and the latest security information received in advance, majority of IDS false positives and attacks that do not affect the system are eliminated. In the event of unauthorized access, our knowledgeable technical experts determine the impact on the system and propose appropriate measures.
- 2. IDS equipment management and maintenance
-
- We verify the signatures and firmware at our end and perform maintenance as needed to keep up with new attack patterns.
- We perform all the operational maintenance, including condition monitoring of IDS equipment.
- Our maintenance staff will perform on-site recovery in the event of hardware failure.
- 3. Reporting and unauthorized access monitoring report
-
- "Emergency Report" - Confirming the nature and impact of the attack. If the risk is determined to be high, we will promptly inform you of the best course of action.
- "Security measures report" - Providing vulnerability information related to the client's system environment.
- "Statistical report" - Monthly unauthorized access monitoring report summarizing trends and countermeasures prepared by our technical experts.
How is our Unauthorized Access Monitoring Service Beneficial to our Clients?
24/7 monitoring of events by IDS significantly reduces security maintenance and operation costs borne by clients.
Accurate emergency reporting and security measure recommendations through the unauthorized access monitoring service helps clients strengthen their security measures.
Strengths of Large-Scale Systems
Our distinctive analysis system analyzes the impact in real time from multiple perspectives such as detection event information, client system environment information and server response information. It is more valuable in mission-critical system environments where high availability is required and a large number of events are detected.
It also supports IPv6 environment.
Analysis by Professional Engineers
Our security experts analyze the events by the client's system environment, communication payload, and attack path to see if the events have an impact on the system. We provide easy-to-understand detection reports and summary reports prepared by our technical experts by combining and aggregating information obtained from IPS products and additional information obtained by us.
Situation-Handling Assistance by Technical Experts
Our security experts scrutinize the detected high-risk events, and if these events are determined to have an impact, provide an emergency report with recommended permanent action plan.
Flow of Unauthorized Access Monitoring (IDS) Service
| Hold a meeting and collect information | Construction | Operation |
|---|---|---|
| Confirm the network environment of customer, information about the environment to be monitored, and contact information according to the content. | Set up the policy according to the information gathered in the interview, verify the operation, and test the connection with the monitoring center. | Emergency reporting of events affecting the system, presentation of reports, signature tuning, etc. |

*This service is registered under "Information Security Service Standards Examination and Registration System" by the Japan Security Audit Association (JASA), a non-profit organization, which conducts the audit and registration.