Next Generation Firewall Monitoring Service
Provides integrated security monitoring using FW, IPS, AntiVirus, etc.
Nowadays, it has become a common practice to prevent a variety of sophisticated cyber attacks through multi-layered protection using multiple security solutions such as firewalls (FWs), IDS/IPS (Intrusion Detection and Prevention System), and antivirus software.
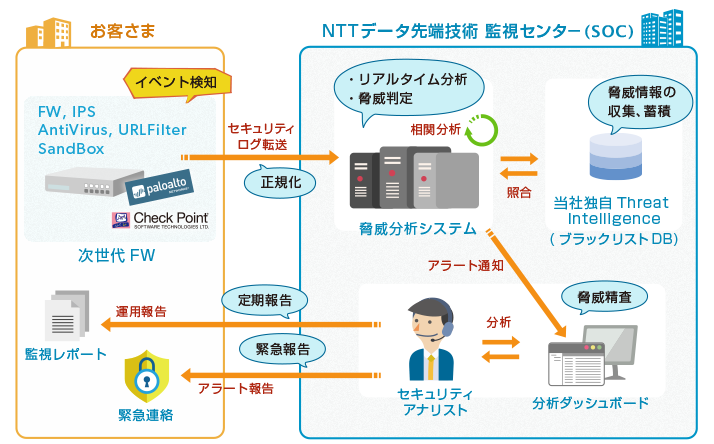
The Next Generation FW Monitoring Service provides customers with integrated security monitoring using multiple functions such as FW, IDS/IPS, antivirus, URL filtering, and sandboxing against a variety of sophisticated threats targeting enterprise applications, data, and users.
Furthermore, the use of virtual appliances makes it possible to provide the service in a cloud environment (AWS and VMware ESXi/vCloud Air are supported).
Challenges in combating unauthorized access
Although security products such as firewalls are generally installed to prevent unauthorized access, is that really enough to provide peace of mind?
Purpose of Firewall
Detect and block unauthorized communications by monitoring data flowing over the network.
Operational issues
Access to permitted ports sometimes even allows attacks to pass through. It is operationally difficult for the administrator to constantly check the logs to determine where an unauthorized access is occurring, and it is also difficult to take immediate action.
Purpose of IPS
"Constantly" check communications over the network on behalf of the administrator. Quickly detect and block unauthorized access that could not be prevented by a firewall and notify the administrator.
Operational issues
- Merely installing the system does not mean that the environment is protected against all threats.
- Signatures need to be tuned.
- Since there are many false positives, determination based solely on IPS device alarms is difficult.
Purpose of Antivirus
Detect and block malware (viruses, spyware) by monitoring data flowing over the network.
Operational issues
Device alerts alone do not tell you what action to take next.
Purpose of URL Filtering
Detect and block access to unauthorized sites by constantly monitoring external web access.
Operational issues
- URL filtering alone cannot protect the environment against all threats.
- Device alerts alone do not tell you what action to take next.
Purpose of Sandboxing
Constantly monitor files flowing through the communication path, and detect and block any unknown malware file found that could lead to a targeted attack.
Operational issues
Device alerts alone do not tell you what action to take next.
Overview of the Next Generation FW Monitoring Service
The Next Generation FW Monitoring Service is provided 24 hours a day, 365 days a year by knowledgeable security engineers.
- 1. Continuous security monitoring and device operation monitoring for 24 hours a day, 365 days a year
-
- Unauthorized access is monitored by carrying out tuning for false detection and erroneous interception of normal communication before providing the service.
- In the event of false detection or erroneous interception of normal communication due to network changes, application modifications, etc. during operation, tuning is carried out based on discussions with the customer and false detection or erroneous interception is eliminated.
- The service detects and reports device malfunctions, etc., by monitoring the operation of the monitoring devices.
- 2. Emergency report sent to customers when critical alerts are detected
- If a high-risk alert is detected and security engineers determine that there is an impact on the systems covered by the service or that there is malware-infected terminal activity on the internal network, an emergency report is immediately sent to the customer.
- 3. Reports on operation and monitoring status
Customer Benefits of the Next Generation FW Monitoring Service
Significant cost savings
Security monitoring of new systems requires a significant cost, including the cost incurred for operators to monitor the systems 24 hours a day, 365 days a year, the cost of operator training, and equipment maintenance cost.
However, by using this Next Generation FW Monitoring Service, our security monitoring center monitors events detected by the next-generation FW, 24 hours a day, 365 days a year, thereby significantly reducing customers' security maintenance and operation costs.
Our proprietary threat information
By comparing alerts generated by monitoring devices, with a database of threat information such as hosts used for attacks, collected using our proprietary methods, we are able to detect communications with rogue servers. Therefore, attacks that would be missed by a stand-alone security solution can be scrutinized from multiple perspectives, thus enhancing security.
Next Generation FW Monitoring Service Deployment Flow
| Hold a meeting and collect information | Monitoring preparation | Operation |
|---|---|---|
| Confirm the network environment of customer, information about the environment to be monitored, and contact information according to the content. | Set up the policy according to the information collected during the meeting, check the operation, and test the connection with the security monitoring center. | Provide emergency report on alerts affecting the system, present reports, update signatures, perform tuning. |
- *All other company names, product names, service names, etc. mentioned herein are trademarks of their respective owners.

*This service is registered under "Information Security Service Standards Examination and Registration System" by the Japan Security Audit Association (JASA), a non-profit organization, which conducts the audit and registration.