Targeted Attack Detection Service "PatoLogphin"
PatoLogphin can easily detect "malware infections" that slip through existing security measures!
PatoLogphin is a service that detects targeted attacks on the office environment by analyzing the logs of NW devices. By automating the analysis system, which is packed with our security operation know-how, we find the slightest sign of a targeted attack from a huge amount of proxy logs that cannot be checked manually. Regular monthly and daily analysis services and spot analysis services are available, which can be easily implemented according to the application without the need to install special equipment.
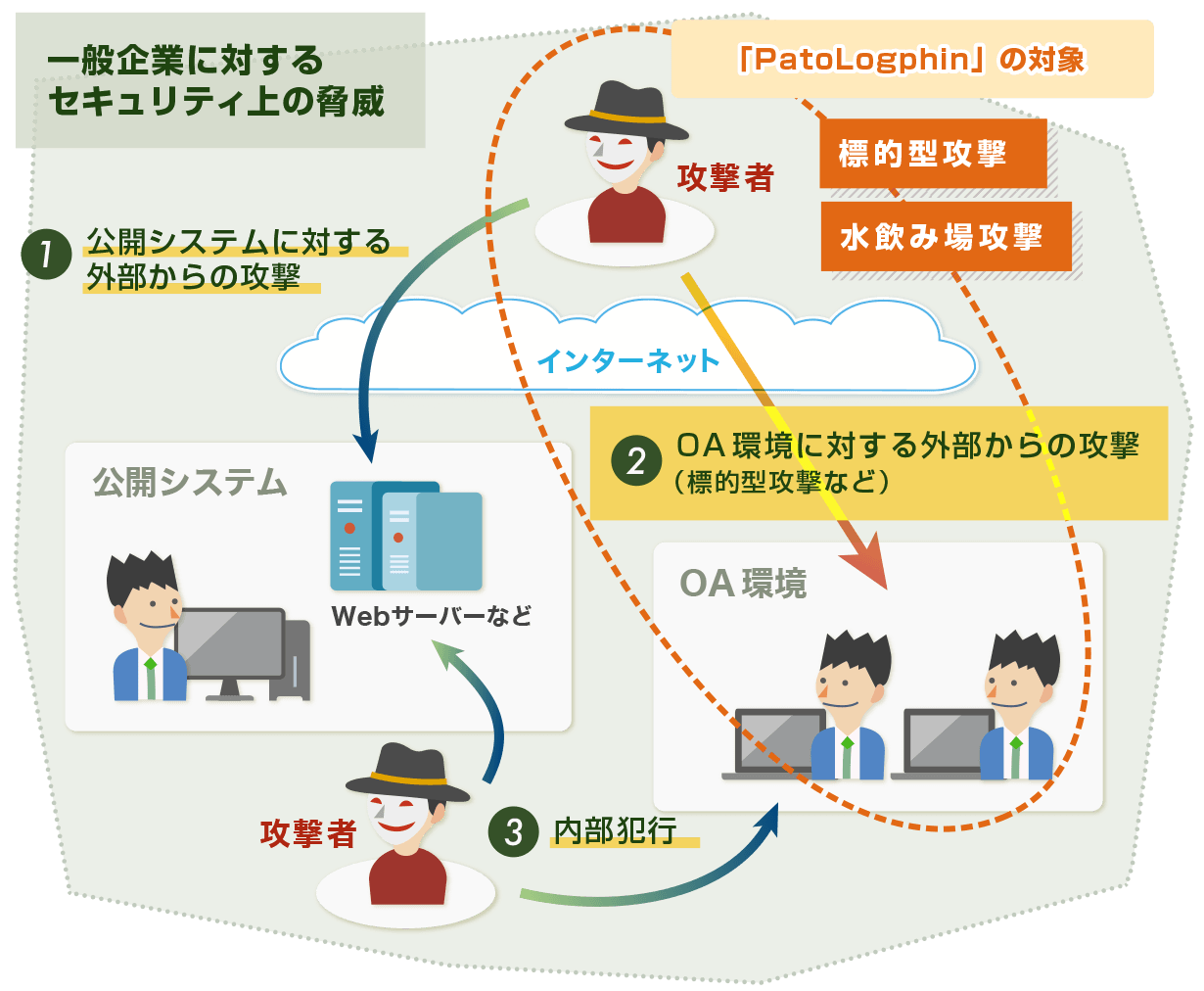
Cyberattacks surrounding company
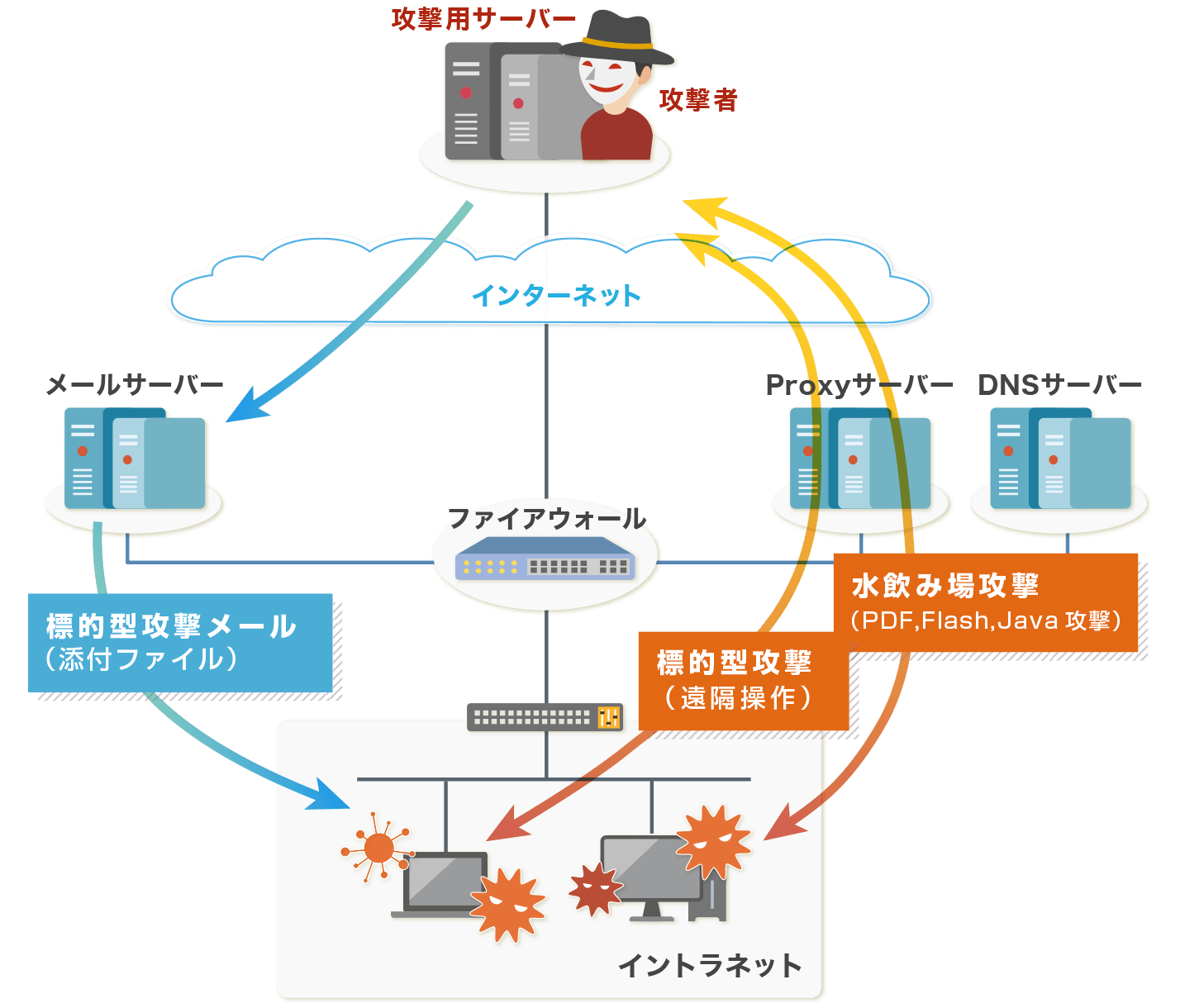
Recently, there has been a sharp increase in the use of malware (viruses and other malicious programs) to steal information from PCs in OA environment, which has a lot of corporate information assets. Unknown malware can bypass existing antivirus and infiltrate OA environment to infect client PCs. Therefore, it is necessary to take "measures in anticipation of intrusion" and "measures for early detection of infection".
Concept of PatoLogphin
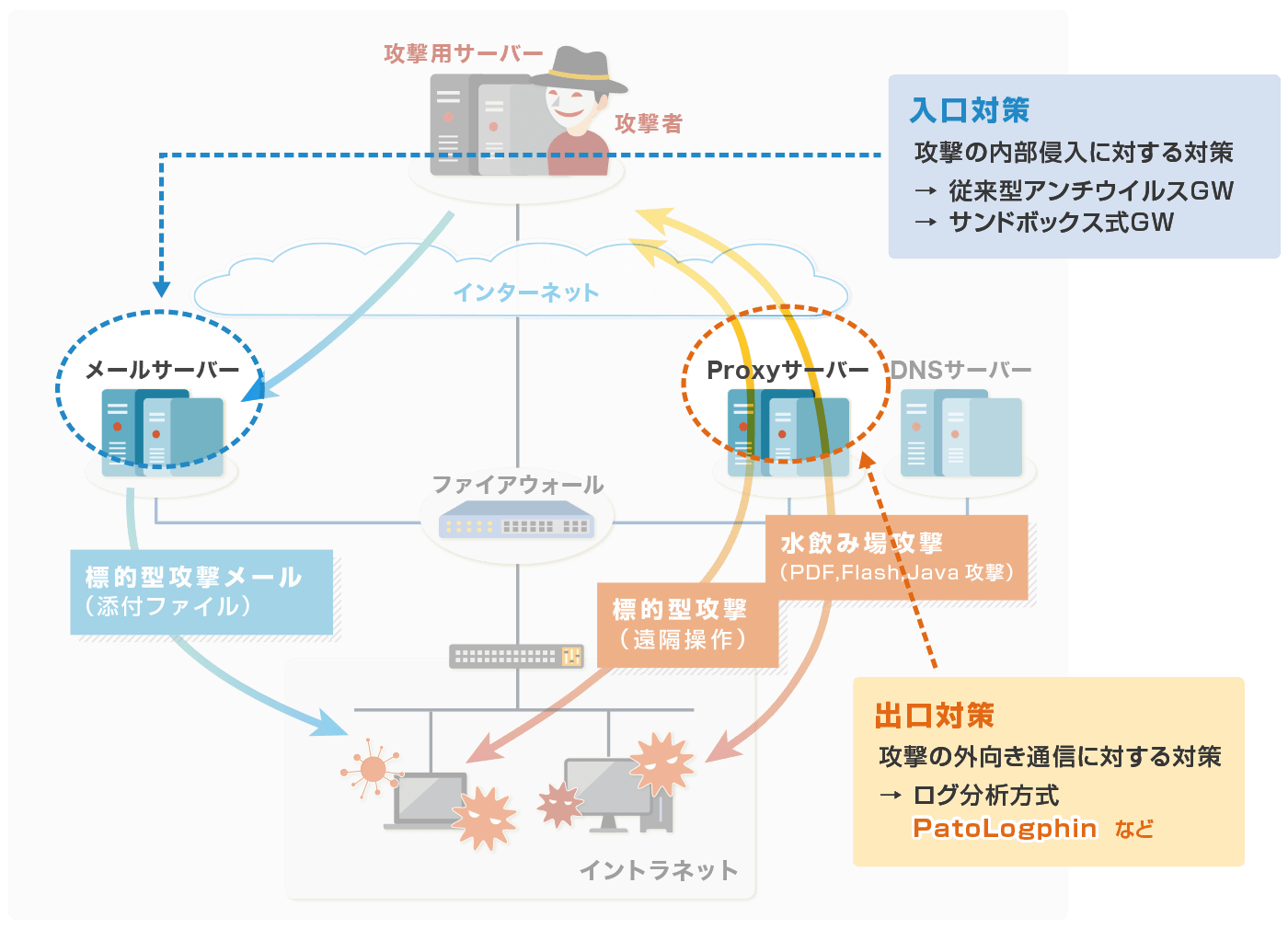
Reinforcement of exit measures in anticipation of intrusion
With the increasing variety of malware and the diversification of intrusion routes, it is difficult to prevent intrusions 100% at the water's edge, so it is necessary to strengthen exit measures in addition to conventional entry measures.
Constant analysis of NW equipment log is effective for early detection
Constant analysis of NW equipment log is effective for early detection of targeted attacks. This analysis service can inspect/analyze entire huge log with high accuracy.
Three know-how for advanced log analysis
- 1. Matching analysis using our own black list
- → We conduct matching analysis using blacklist owned by NTT DATA Group to detect communication with C&C server.
- 2. Advanced analysis using detection patterns developed by us
- → We find signs of targeted attacks in huge logs by developing high-security systems and using the results of research and development
- 3. Advanced analysis based on the know-how of our analysts
- → Experienced engineers who have dealt with real and sophisticated cyberattacks investigate/analyze and determine the scope of the attack and how to respond to it.
Overview of PatoLogphin
- 1. Log analysis
-
- Analyzes proxy logs to determine whether malware infection is caused by targeted attacks
- Supports not only the malware infection stage, but also "surveillance" stage attacks before malware infection and unknown attacks called zero-day attacks
- Can conduct retrospective analysis
- Easy to install because implementation is possible as long as logs are available
- 2. Provision of information
-
Daily alert contract
- Sends e-mail notification (if daily plan is selected) when an attack is detected
When the attack is detected, e-mail notification reports the "IP address of the terminal" suspected of being infected with malware, "the degree of infection", and "the recommended emergency response measures".
- Sends e-mail notification (if daily plan is selected) when an attack is detected
-
Monthly reporting contract (periodic or one-shot)
- Provides monthly reports summarizing monthly information
- In addition to a summary of the current month analysis results, the monthly report provides medium- and long-term recommended countermeasures and the version of outdated software in use in the customer environment.
- 3. Tuning/updating detection patterns
-
- Tunes/updates detection patterns according to the latest attack trends
Improved Monthly Report
Individual Analysis
- Reports presence of malware infection
-
- When the attack is detected, in addition to the IP address of the affected terminal, the degree of risk ("high", "medium", or "low") and emergency response measures according to the progress of the attack in the customer environment are also reported.
- In addition to the contents of the report when attack is detected, the event that occurred and the infection process are explained.
Overall Analysis
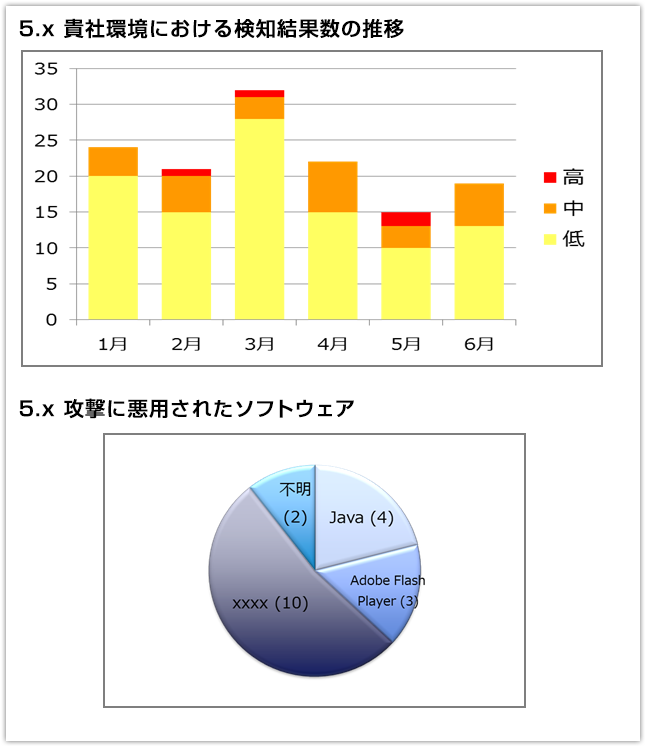
- Reports detection trend
-
- Provides information on the number of detection results during the period when service is used
- Explains the analysis result of the attacks in the current month in entire company, including the name of the software that was misused, based on the customer environment, and the measures taken to respond to the attacks
- Visualizes software usage
-
- Visualizes old assets that are no longer provided with patches using information obtained from Proxy logs based on information such as the OS version or JAVA version installed on the terminal
Features of PatoLogphin
| Easy installation | High detection performance | Specific reports | Visualization |
|---|---|---|---|
| As long as you have PatoLogphin, you can use the service. Service can be installed in a short period of time | High detection accuracy is achieved by utilizing large amounts of malware information held by NTT Group | Specific and easy-to-understand reports on appropriate measures to minimize damage | Analyzes and visualizes device status (software version, access to SNS sites, etc.) |