INTELLILINK Encryption Solutions
(Applicable Product: Check Point Full Disk Encryption)
Strong authentication and encryption prevent the information leakage due to theft or loss of client PCs.
Theft or loss of PCs is a major cause of leakage of important information such as personal information.
Check Point Full Disk Encryption prevents information from being decoded and strongly protects information leakage by authenticating the login before OS startup and encrypting the entire hard disk. Since it can be installed and operated without a dedicated server, high installation effect can be achieved in a short period of time.
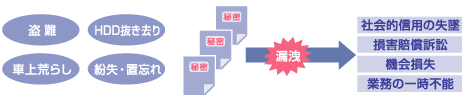
Information leakage risk involving PCs
When PCs are taken outside the company or used for mobile purposes, there is a risk that the information on the disk may be decoded and leaked in various cases. In addition, if your personal information is diverted or misused, you may be both a victim and a party at a fault.
Features and Functions of Check Point Full Disk Encryption
- 1. Easy installation
-
- Centralized user management with existing file servers
- It can be stand-alone
- Batch installation, batch setting of security policies
- Hierarchical management is possible according to user organization or users
- Cost reduction by eliminating the need to build a dedicated server
- Less burden on the administrator even in large-scale operations
- Company-wide distribution in a short period of time
- Smooth installation/operation/management
- 2. Strong authentication
-
- Log-in authentication before OS startup
- Account lock function limits the number of login attempts
- Effective as a countermeasure against Windows cracker tools
- Effective as a countermeasure against password brute-force attack
- Reduced burden on user
- 3. Disk encryption
-
- Encryption of the entire hard disk including OS and file areas
- Encryption/decryption is automatic
- The encryption algorithm uses 256-bit length symmetric key ciphers "Blowfish256bit" and "AES256bit".
- Reliable protection of information on disk
- Prevents the user from forgetting the encryption
- Users use PCs normally without being aware of encryption
- High encryption technology
- 4. Easy policy management
-
- Administrator can set/enforce the policy
- User cannot change settings or uninstall
- Regular password changes
- Enforcement of password setting rules such as mixed alphanumeric characters
- Account expiration date setting
- Easy to manage/enforce policy
- 5. High reliability
-
- Federal Information Processing Standard "FIPS140-2" certified product
- A global standard Common Criteria EAL4 (equivalent to ISO15408) certified product
Check Point Full Disk Encryption Hierarchy Management Example
Flexible management structure according to the organization and the number of users, and its installation and operation are smooth.
Flow of Check Point Full Disk Encryption Installation
| Prior hearing | Installation | Help desk |
|---|---|---|
| We interview the customer to know about PC usage and determine the installation schedule. | Based on the content of the interview, we finalize the profile settings necessary for installation and we start the installation using the installer. | - Q&A over telephone - Support for forgotten password - Support for defective products *This is our helpdesk service. |
Check Point Endpoint Security Full Disk Encryption is a registered trademark of Check Point Software Technologies.
*All other company names, product names, service names, etc. mentioned herein are trademarks of their respective owners.