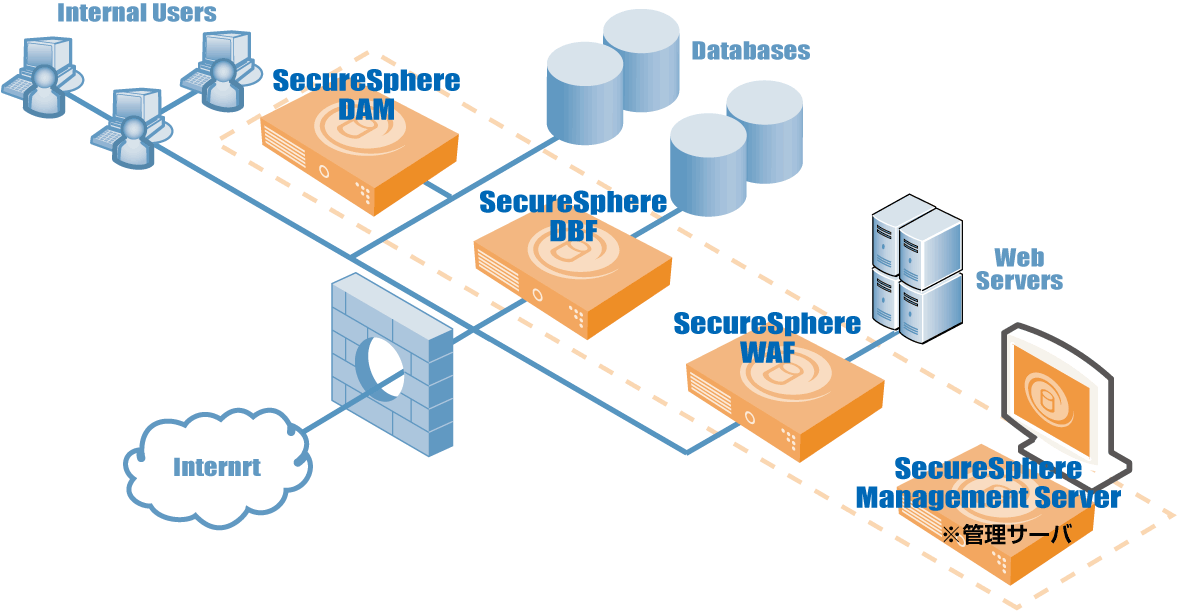
Web/DB Solution SecureSphere
Automated appliance for monitoring, auditing and defense in web systems/DB
SecureSphere®detects and provides protection against attacks on web applications. Furthermore, by monitoring and auditing both internal and external access to the database, it is useful for internal control and prevents information leakage caused by unauthorized access.
Automation technology that minimizes manual work reduces the burden on administrators and reduces installation and operation costs.
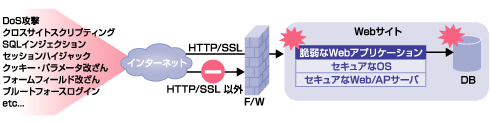
Issues in Web Application Vulnerability Measures
The attacks on web applications cannot be detected and prevented by conventional network firewall because they use http ports that are publicly available. Therefore, even if the OS and server program settings are secured and security patches are applied as needed, a vulnerability in the web application may lead to information leakage.
Overview and Functions of SecureSphere
SecureSphere Product Lineup
- Web Application Firewall (WAF)
- WAF detects and blocks attacks aimed at vulnerabilities in web applications running on web servers.
- Because it provides protection against attacks in front of the web server, it can protect web systems that are difficult or time-consuming to modify.
-
- Automatically updates the latest attack patterns and worm signatures, which are equivalent to a blacklist and provides protection against known attacks.
- Automatically learns URLs, parameters, form fields, etc., which are equivalent to a white list and automatically generates policies for each application. It provides protection against unknown attacks by eliminating communication that does not conform to the defined policy.
- Database audit system Database Activity Monitoring (DAM)
- DAM evaluates the database system infrastructure for vulnerabilities and monitors and records database access activities.
- It can properly manage and store the audit logs, and is also effective for internal control.
-
- Monitors and records all DB accesses and responses.
- Can identify and record not only the applications accessed, but also who accessed what data and when.
- Automatically learns daily internal and external accesses, including Telnet and SSH accesses by internal parties, and judges, detects and notifies abnormal access based on the automatically created profile.
- Can generate more than 70 types of reports such as U.S. SOX, PCIDSS, and HIPAA compliant reports and warning analysis reports.
- Audit logs can be sent via e-mail and generated in HTML, CSV, and PDF formats.
- Database Defense System Database Firewall (DBF)
- DBF protects databases from external attacks via web applications and information leakage due to internal unauthorized access.
- In addition to monitoring and auditing function, it provides a defense function to block unauthorized access accurately and immediately. (including WAF and DAM functions)
-
- Instantly determines whether a user has committed a harmless act and immediately blocks unauthorized access by integrated correlation analysis of a black list covering SQL protocol anomaly detection and known attacks, a white list based on automatically generated user profiles, and multiple events.
- In addition to automatic user profile policy settings, administrators can create custom policies to identify and control access to sensitive data users. (Restrict access to files, prevent unauthorized use of IDs, prevent unauthorized intrusion from external networks, etc.)
Key Functions of SecureSphere
- Dynamic profiling technology
-
- Dynamic profiling technology automatically monitors all interactions between users, web servers, and databases, and builds profiles of application configuration and normal behavior.
- It identifies and protects against various types of potentially malicious activity through comparison of actual traffic with profile.
- Continuous learning algorithm can automatically detect application changes, requiring minimal manual adjustments or configuration changes.
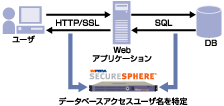
- Universal user tracking technology
-
- Universal user tracking technology correlates and analyzes web and DB communications and associates web application login IDs with access to the DB.
- With this technology, access to DB can be identified down to the user, whereas previously it was only possible to track down the access to the web application.
- It supports major databases and various web applications including Oracle EBS and SAP.
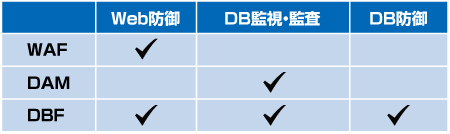
- WAF Web Application Firewall
- DAM Database Activity Monitoring
- DBF Database Firewall
SecureSphere Installation Example
Non-inline sniffer configuration (compatible with DAM)
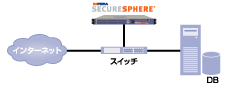
- Sniffer can be deployed without shutting down the network
- No need to change existing environment (IP address is not required)
- Ideal for verification and early installation
- Centralized management of multiple segments
*Requires a SPAN port such as a tap or switch.
In-line bridge configuration (compatible with WAF/DBF)

- No need to change existing environment (IP address is not required)
- Verification by detection-only simulation mode is possible
- After verification, blocking starts by switching to defense mode
- Maintains availability with fail-open function
Flow of SecureSphere Installation
| Prior hearing | Trial Installation | Production Installation |
|---|---|---|
| Conduct interview to know about security status of customer. Collect and analyze individual monitoring information. | • Introduce on a trial basis in a detection-only mode. • Create profile by automatic learning. (about 1-2 weeks) |
• Develop/establish the policy based on test results. • Switch to defense mode and start operation. |
*SecureSphere is a registered trademark of Imperva.
*All other company names, product names, service names, etc. mentioned herein are trademarks of their respective owners.