Vulnerability Management QualysGuard
Prevents leakage of confidential data over the network
QualysGuard enhances enterprise network security and enables documentation of policy and regulatory compliance.
Issues in Vulnerability Countermeasures
Implementing vulnerability countermeasures continues to put an enormous burden on many companies.

Vulnerability Management Overview
While new security vulnerabilities are increasingly being found, the time taken for methods of misusing these vulnerabilities (such as manual attacks, worms, viruses, Trojan horses) to emerge and share is becoming shorter and shorter. As a result, it is no longer sufficient to conduct the company network audit once a year or once a quarter.
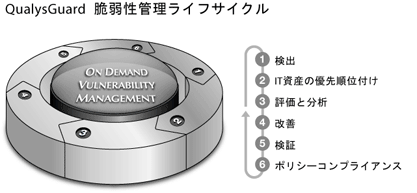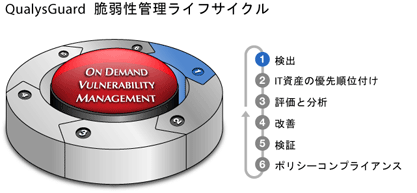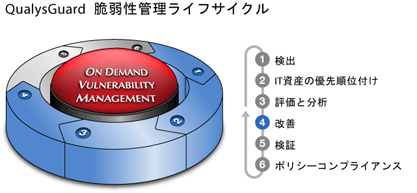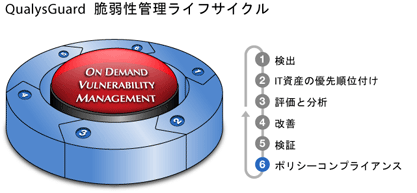
- (1) Detection
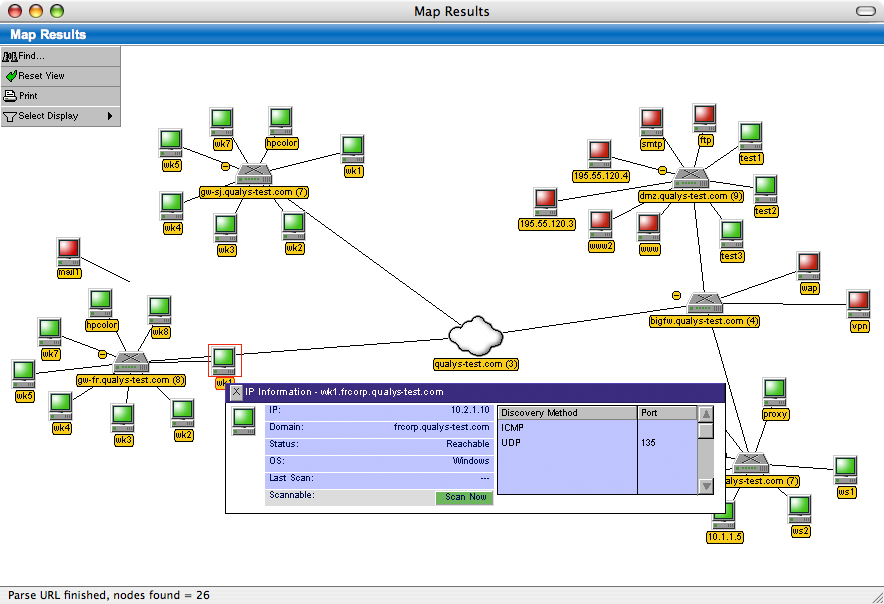
- QualysGuard discovers all IT assets on the network and identifies detailed information about the host such as operating systems and open services.
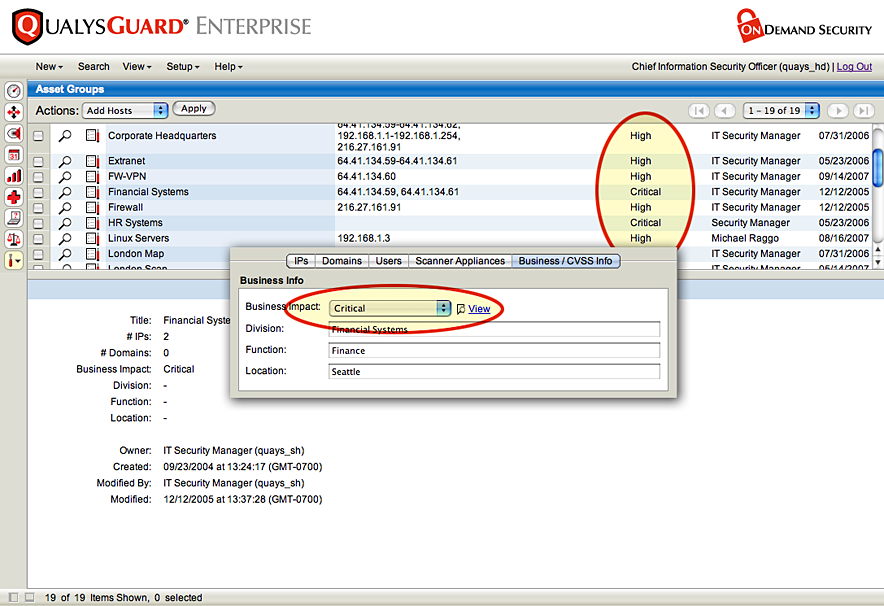
- (2) Prioritization of IT Assets
-
- It manages the network by categorizing IT assets by group or department.
- Assigns business value to IT assets based on their severity to the business.
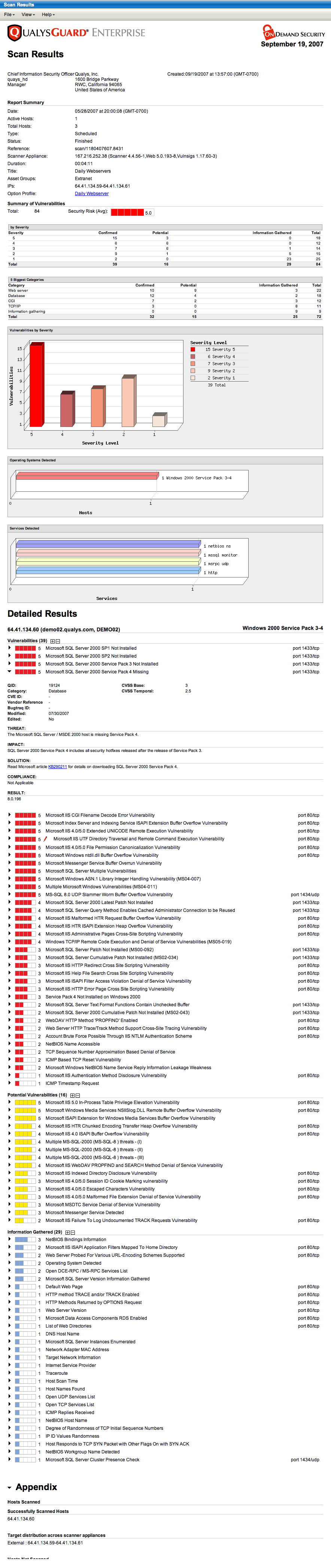
- (3) Evaluation and analysis
-
- QualysGuard determines a baseline risk profile so that risks can be eliminated depending on the criticality of the IT assets.
- Identifies security vulnerabilities through regular automated schedules.
- Measures the business risk level of IT assets according to the security policy.
- Analyzes trend of overall security conditions over time.
- (4) Improvement
- QualysGuard prioritizes and fixes vulnerabilities according to business risk.
- (5) Verification
- QualysGuard verifies through post audits that threats have been removed.
- 6) Policy Compliance
-
- QualysGuard establishes security policies, processes, and standards necessary for compliance with government regulations and corporate policies.
- Secure audit trail and trend analysis help achieve compliance and pinpoint newly arising issues.
Functions and Features of QualysGuard
QualysGuard can automate all steps of the vulnerability management lifecycle process, allowing companies to enhance network security, automate security audits, and ensure compliance with external regulations and internal policies.
QualysGuard, an on-demand solution can be deployed anywhere in the world in few hours and provides immediate visibility into security and compliance status. QualysGuard is the world's most widely installed on-demand security solution, performing 150 million IP audits annually.
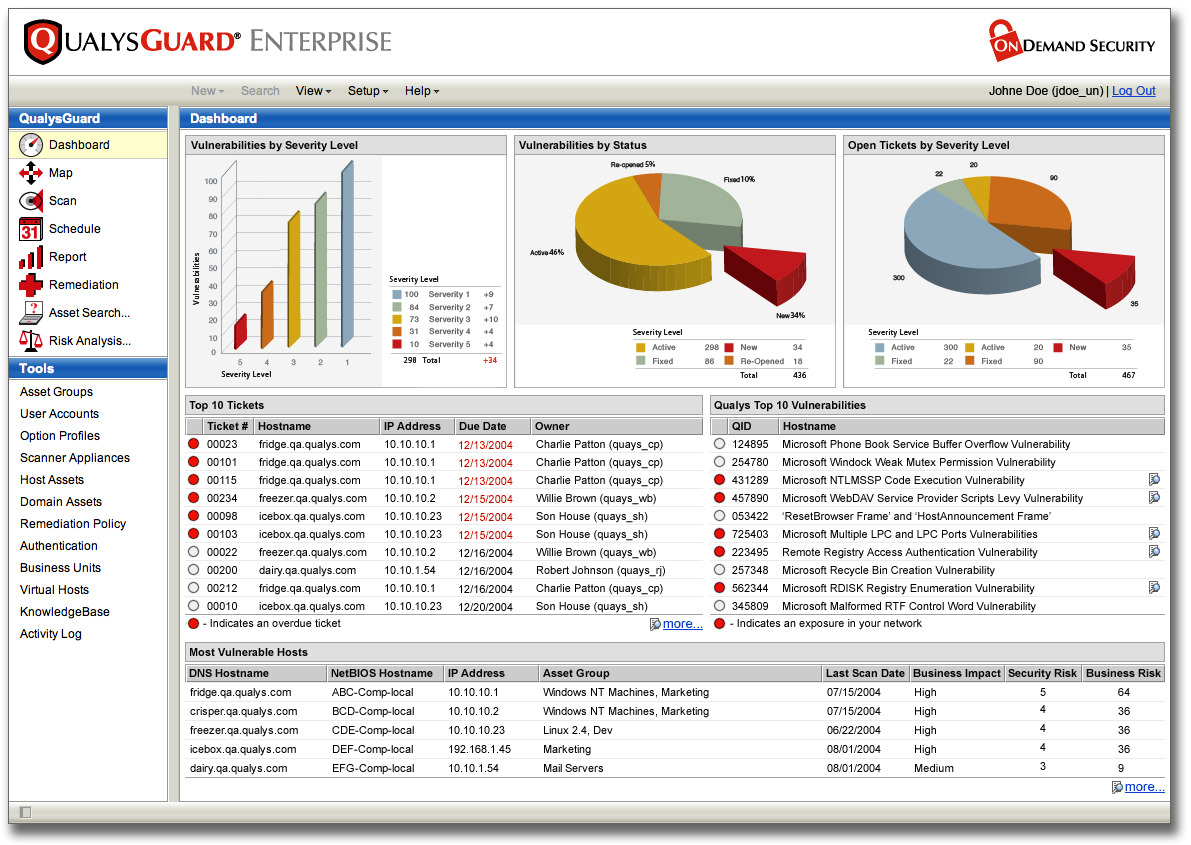
- Discovers and prioritizes all network assets
- QualysGuard identifies all network devices and software applications present in the infrastructure and identifies details about the host, such as operating systems and open services.
- Manages and mitigates business risks
- QualysGuard reduces risk by automating vulnerability identification and improvement prioritization based on mission-critical systems and high severity vulnerabilities.
- Ensures compliance with laws, regulations, and corporate security policies
- QualysGuard documents regulatory compliance based on the certainty of agent-less automated audits, tamper-resistant audit trails, and third-party assessments.
- Establishes PCI DSS (Payment Card Industry Data Security Standard) compliance
- QualysGuard testing and compliance application achieves PCI compliance status.
*All the company names, product names, service names, etc. mentioned herein are trademarks of their respective companies.