Web Isolation and Sanitization Solution - Menlo Security

Prevent Targeted Attacks with Isolation and Sanitization Technology
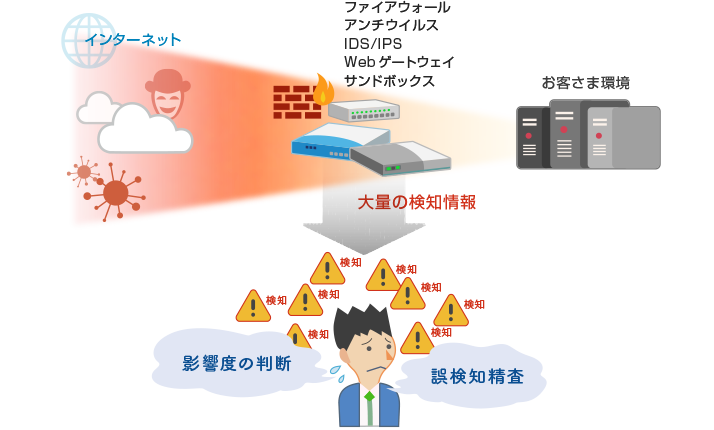
As more and more companies are adopting several security products based on the concept of multi-layered defense, they are required to reduce inaccurate detection information and focus on addressing more important detection information.
Unlike conventional detection-based security products, the Menlo Security web isolation and sanitization solution isolates and detoxifies the client's web-based content in an isolated environment and returns it to the client. This reduces the large amount of detection information generated by other devices and is an effective preventive measure against targeted attacks.
Challenges of Detection-based Security Products
Overview of Menlo Security
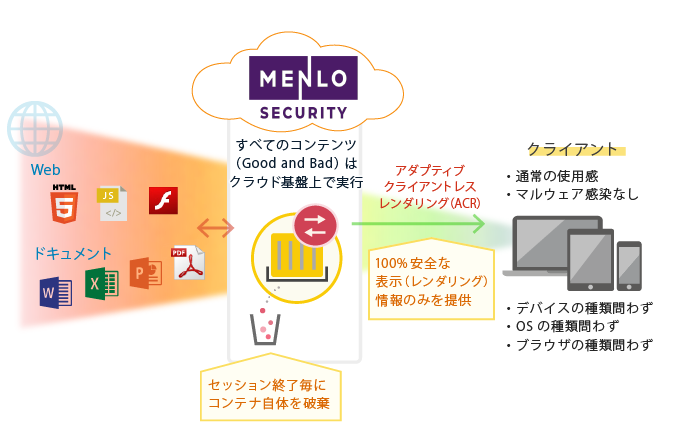
Menlo Security is a new type of security product. This product falls under the category of targeted attack countermeasures called "sanitization" or "network isolation." Menlo Security's patented rendering technology, ACR (Adaptive Clientless Rendering), eliminates the threat of malware infection that occurs when browsing web content.
It runs the client's web content on a cloud-based infrastructure isolated from the office environment and sends only secure rendered (displayed) information to the user's device.
Malicious content, if any, is rendered harmless through Menlo Security, which enables clients to access web without needing to determine (detect) the safety of the content.
Features of Menlo Security
- Preventing targeted attacks
- Among the countermeasures of "prevention," "blocking," "detection," and "forensics," Menlo Security is a product that focuses on "prevention."*
Many conventional security products analyze threat information and provide it as detection information. Information security managers then need to analyze the detection information to come up with countermeasures.
Menlo, on the other hand, sanitizes Web communications, which eliminates the need for information security managers to spend a great deal of effort on analyzing detection information, isolating false positives and negatives and prioritizing countermeasures.
*Menlo Security is positioned as a "prevention" measure in the "Delivery" stage of access control in the "cyber kill chain," which describes the sequence of attacker actions in a targeted attack.
http://www.macnica.net/solution/security_apt.html/
(Macnica, Inc.: Targeted Attack Prevention) - Extremely easy to implement
- Since Menlo Security is a SaaS offering based on a cloud-based infrastructure, it is an extremely easy-to-deploy product. You simply need to set Menlo Security as the proxy server to complete the installation process.*
*In order for an encrypted website to go through Menlo, an SSL certificate must be installed on the proxy. - No client configuration, server or software installation required
- Menlo Security requires no configuration on the client. There is also no need to install separate servers or software in the office environment. You simply need to set Menlo Security as the proxy server to complete the configuration.
- Supports various environments
- Menlo Security supports several environments. This product can be used on any OS, browser, or device, as it does not require client-specific configuration.
- Comparison with virtualization products
- Products that isolate and secure the office environment include virtualization products such as virtual browsers and virtual desktops (VDI). Menlo Security is superior to virtualization products because the total cost is relatively low, it guarantees the same ease of use as a regular Internet connection and puts less operational burden on the administrator.
Menlo Security Implementation Flow
Menlo Security being a SaaS offering, it can be implemented smoothly in the manner described below. The system can be implemented in as little as one month before the production environment is available for use.
| PoC | Installation | Operation |
|---|---|---|
| We will provide an environment equivalent to production (approximately 2 weeks from application). Please check the user experience. The client shall then conduct verification (2-4 weeks). | Client will be required to perform the necessary operations for the implementation of the system. Our security experts will provide operational assistance through a prompt and continuous system. | Our security experts will provide operational assistance through a prompt and continuous system. |
- Menlo Security is a registered trademark of Menlo Security, Inc.
- *All other company names, product names, service names, etc. mentioned herein are trademarks of their respective owners.