Vulnerability Management Platform Tenable.io
What is Tenable.io?
Tenable.io Vulnerability Management (hereinafter, "Tenable.io") is a cloud-based vulnerability management platform built on advanced Nessus Vulnerability Assessment technology by Tenable Network Security.
Challenges in Vulnerability Prevention
- The company organization has unmanaged IT assets (such as server equipment, network equipment, etc.) and risks cannot be managed properly.
- The IT assets of organization are exposed to new threats every day, making it difficult to maintain security with vulnerability diagnosis conducted once a year.
- Many IT assets need to be managed and the overall security status of IT assets cannot be assessed accurately.
- Many vulnerabilities are detected and prioritizing vulnerabilities to be addressed becomes time consuming.
What can be achieved with Tenable.io?
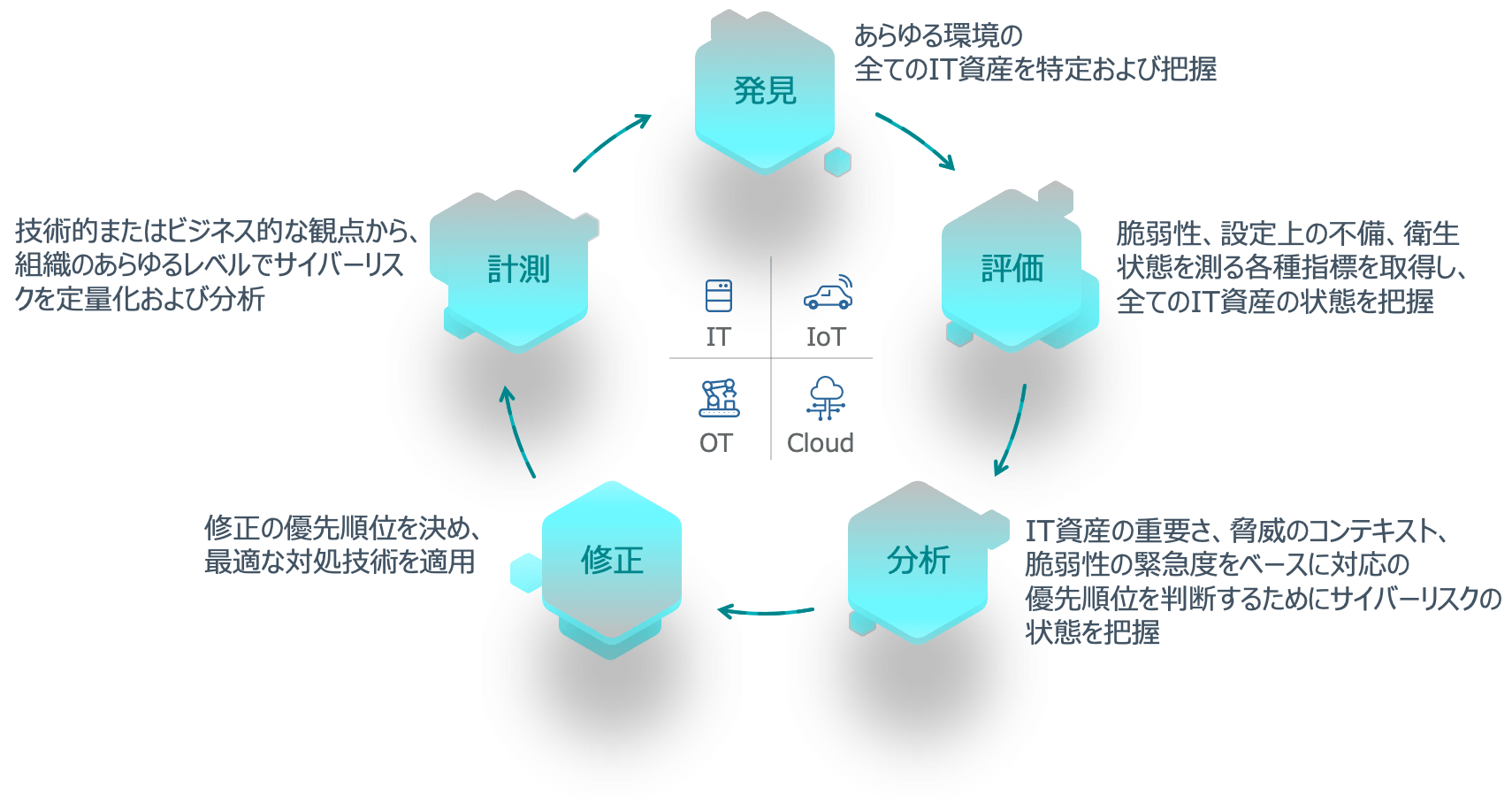
By performing continuous vulnerability scans for IT assets of the company organization and evaluating and analyzing the scan results, you can visualize the security status and compliance status of your IT assets and properly manage vulnerabilities.
Vulnerability Management Lifecycle
Features and Functions of Tenable.io
(1) Supports multiple scanners for a wide range of IT environments
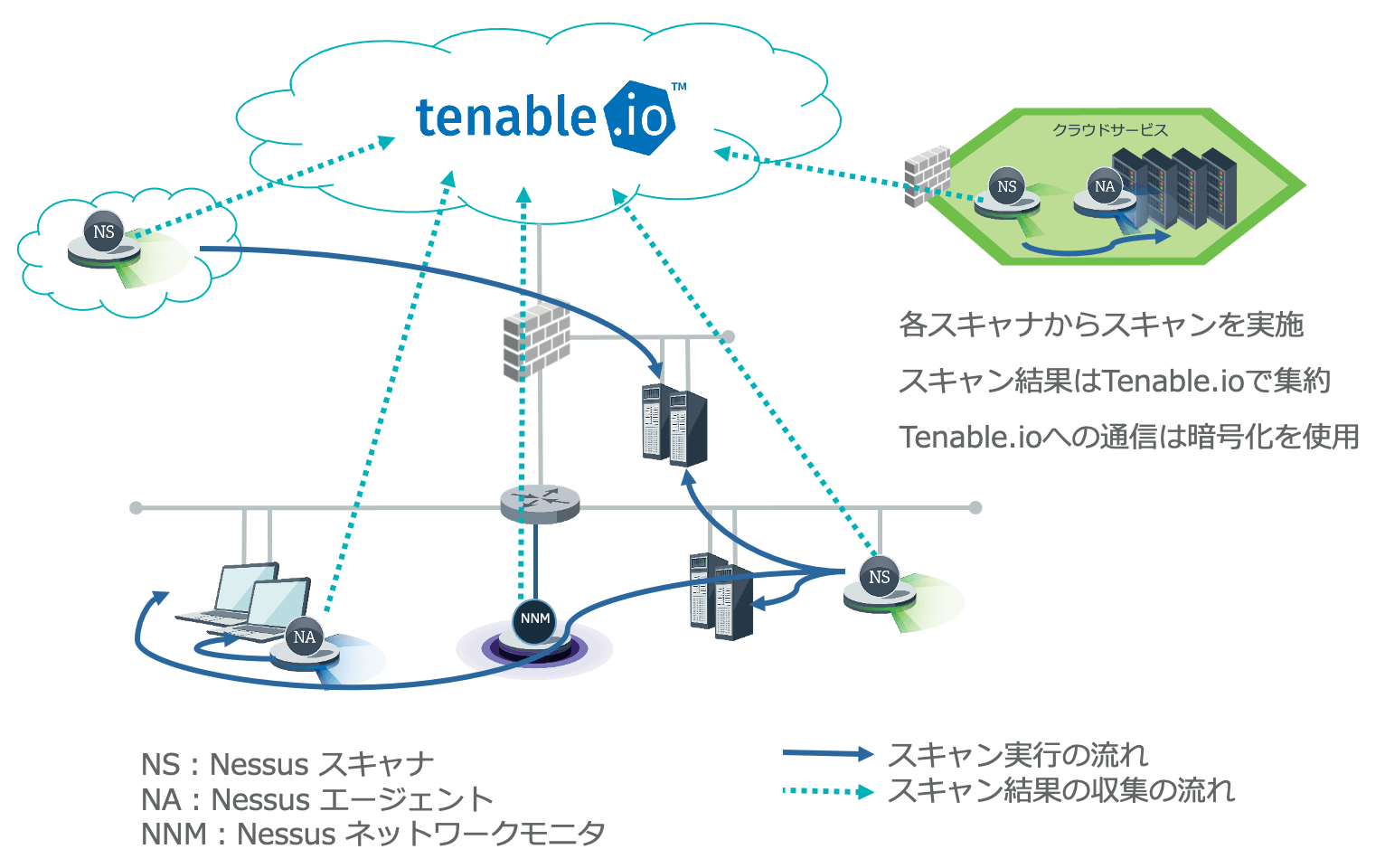
Tenable.io supports the following three types of scanners depending on the IT environment of customer.
| Scanner Type | Scanner Method | Strengths |
|---|---|---|
| Nessus Scanner | Used by deploying on the cloud or internal network | Scanning over the network enables detection of vulnerabilities in services exposed to the network |
| Nessus Agent | Used by installing on Windows, Mac, Linux, and other systems | Capable of detecting vulnerabilities in the system that cannot be detected by scanning over the network |
| Nessus Network Monitor | Network traffic is monitored by connecting to network equipment | Can perform unloaded scanning of equipment such as IoT and detect unmanaged terminals present in the organization |
Arrangement of each scanner in Tenable.io
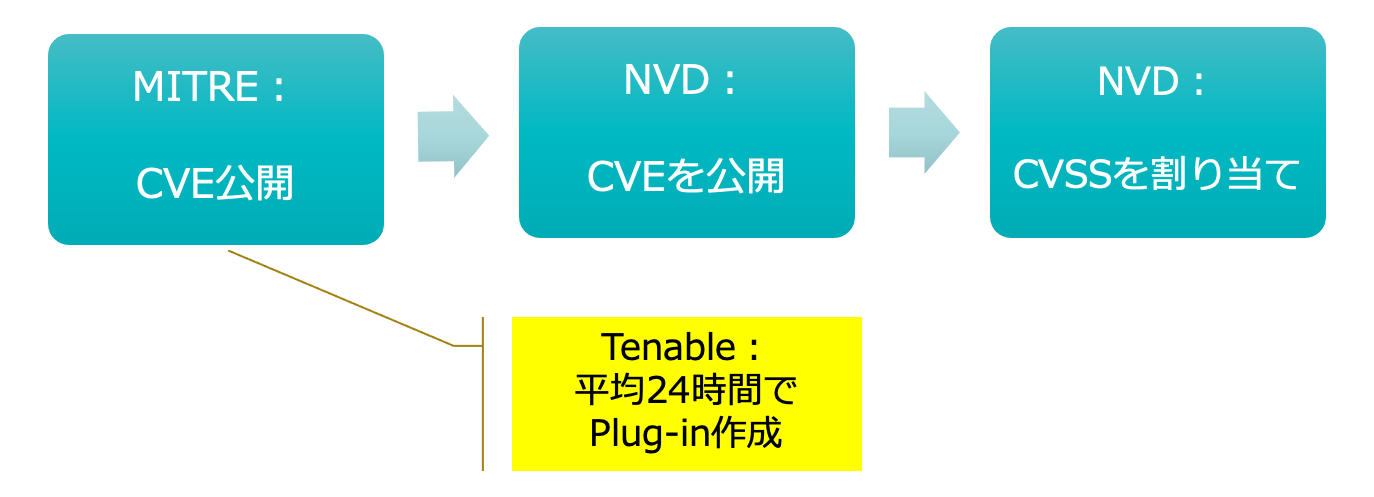
(2) Constantly collects vulnerability information and automatically updates vulnerability plug-ins (attack pattern information)
Tenable.io constantly collects vulnerability information and automatically updates vulnerable plug-ins within 24 hours after MITRE releases the vulnerability information (CVE number). This enables early response to new threats, such as zero-day attacks, and reduces the risk of attacks and malware infection.
- MITRE: A non-profit research organization in the U.S. that assigns "CVE" number, which is a globally-used vulnerability identifier.
- NVD: Abbreviation for National Vulnerability Database. Vulnerability information database managed by NIST (National Institute of Standards and Technology)
(3) Implements the industry's first priority vulnerability prediction function
Tenable.io implements the industry's first priority vulnerability prediction function, which uses a unique VPR (Vulnerability Priority Rating) scoring system to prioritize vulnerability countermeasures. This feature enables prioritization of vulnerabilities based on threats and narrows down the number of vulnerabilities that need to be addressed at an early stage to 3%, which significantly reduces the time to respond to vulnerability.
Analyzes seven different categories*and 150 different elements based on our own data science.
*Past threat sources, past threat patterns, vulnerability measurement metrics, vulnerability metadata, past threats, affected vendors, exploit availability
Continuously tracks over 109,000 vulnerabilities and responds to risk fluctuations in real time.
Determines the vulnerabilities that are expected to be exploited within 28 days as priority target.
97% reduction in the percentage of urgent vulnerabilities compared to the widely adopted CVSS.
(4) Analyzes data with advanced search function
The information on IT assets and vulnerabilities collected and detected by Tenable.io can be extracted using various conditions for different applications, which reduces operational cost associated with data analysis.
- Identification of specific IT assets
- By assigning random tags to IT assets, such as location, department name, or system administrator name, applicable IT assets can be searched based on the information assigned to the tag.
- Investigation of specific vulnerabilities
-
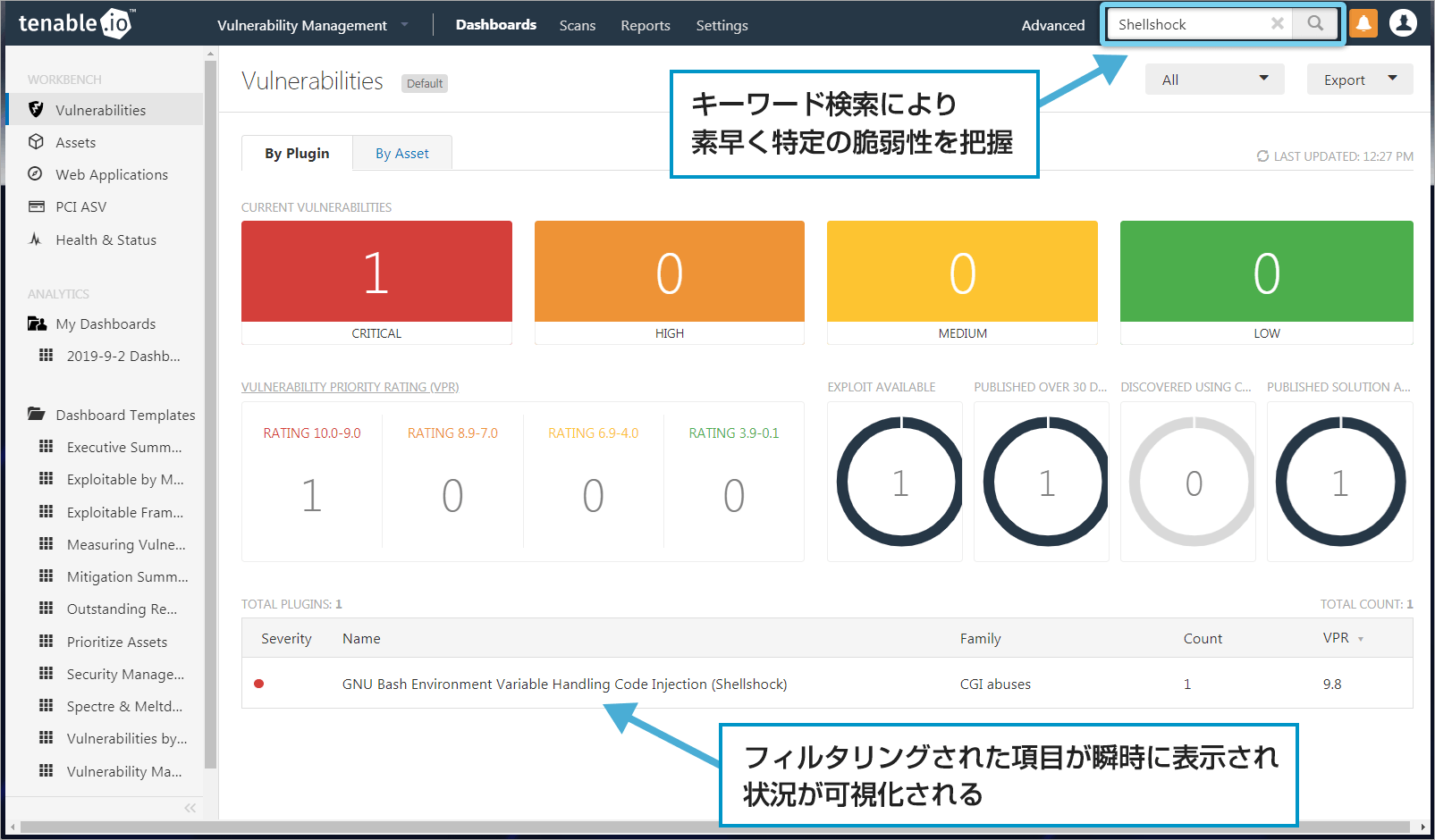
From the detected vulnerabilities, you can search for specific vulnerabilities by keyword search, or using conditions such as CVE number and validity of attack code with the search function.
You can instantly identify specific vulnerabilities inherent in your organization. From the chronological display and priority level display, you can immediately determine the response status and whether a response is required.
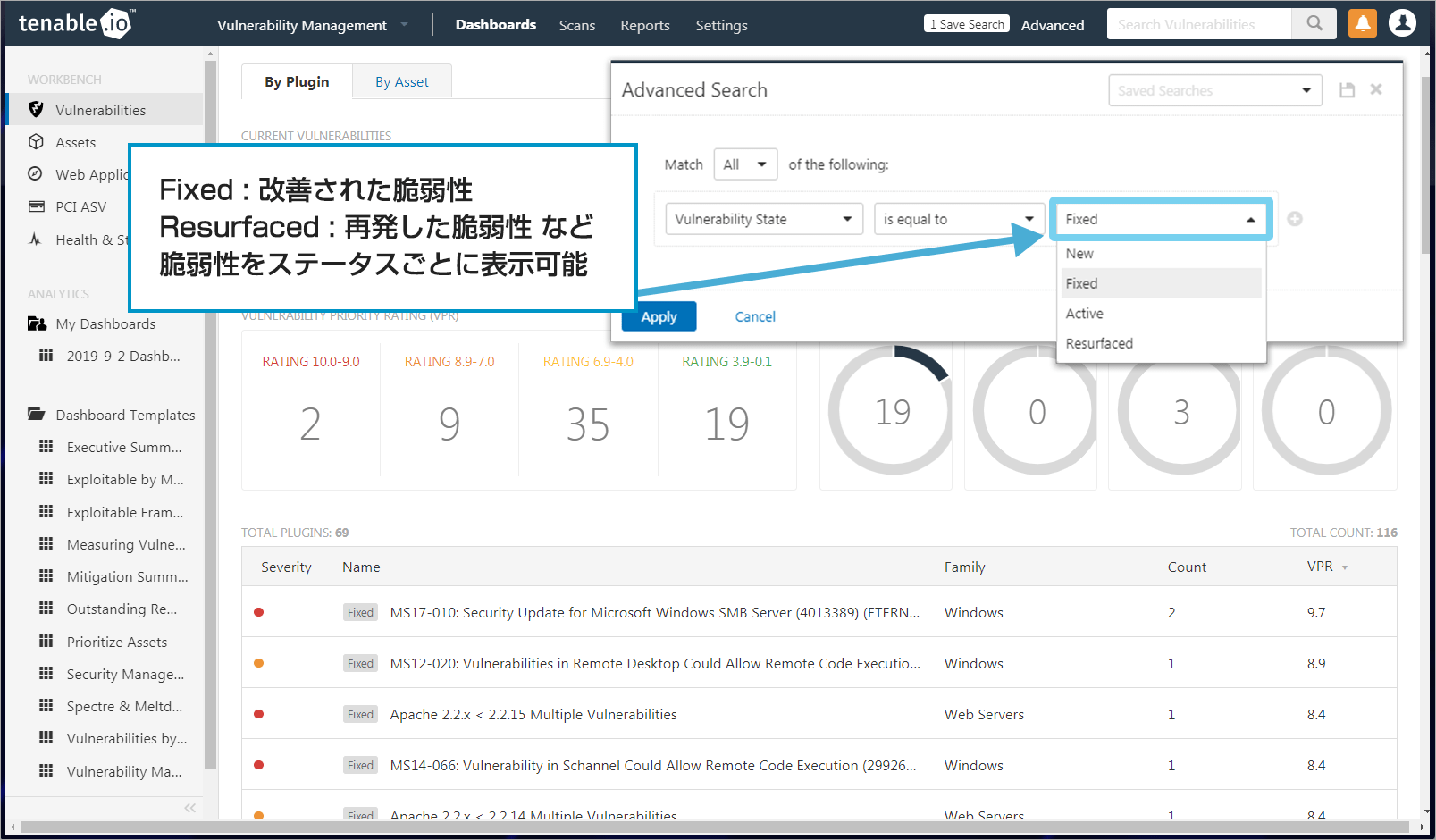
- Identification of improved and recurrent vulnerabilities
-
For detected vulnerabilities, you can check whether they are newly discovered vulnerabilities or recurrent vulnerabilities. You can also determine the extent to which vulnerabilities have been improved.
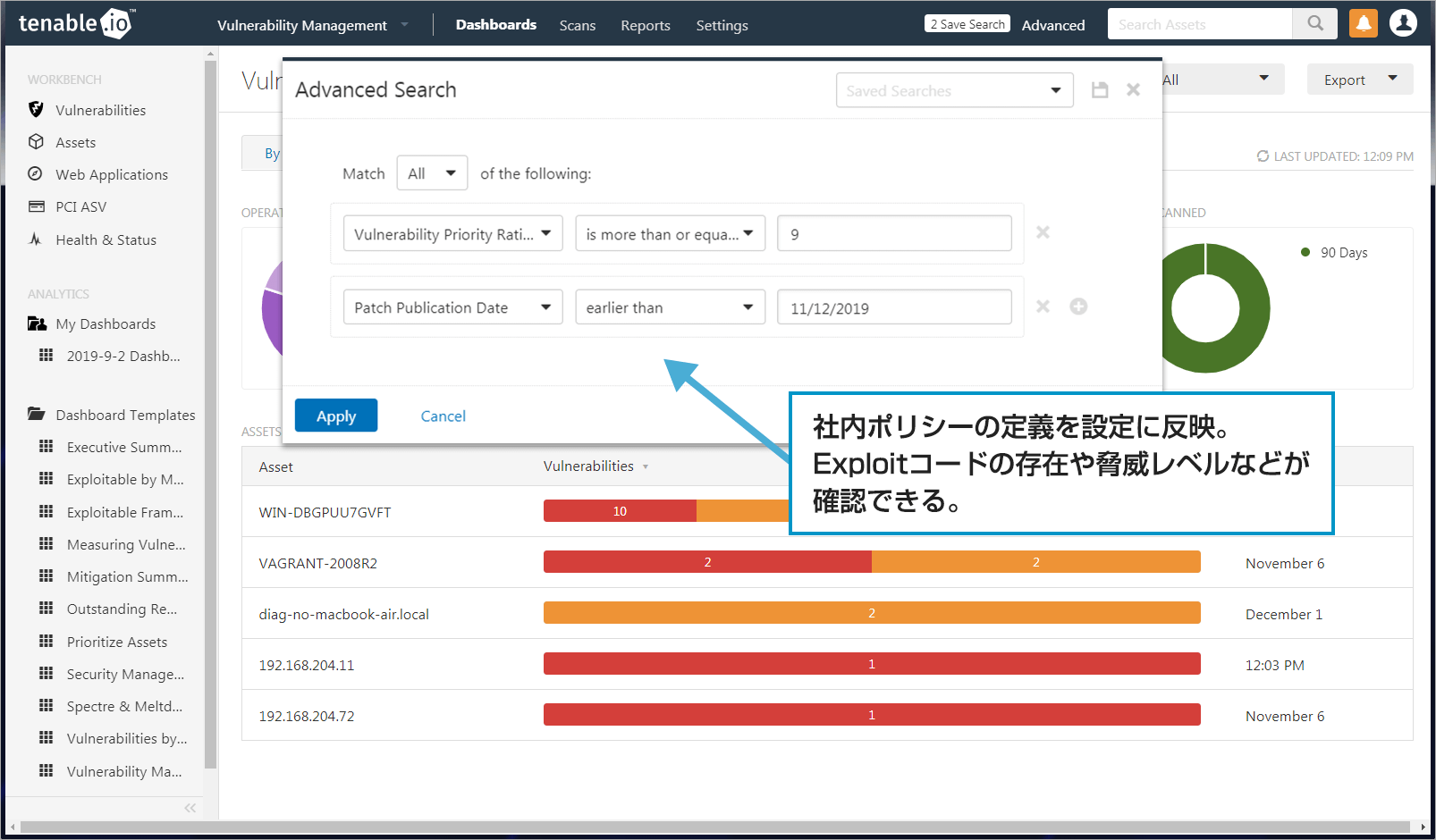
- Investigation of terminals violating the policy
-
You can search for terminals that violate predefined policies in your organization.
(5) Manages cyber risk across the organization with Tenable Lumin (optional)
Tenable Lumin allows you to effectively measure cyber risk and evaluate it against organization within the company or a competitor in the same business.