We propose the "Zero Trust" model of security measures to address the new challenges in cybersecurity faced by companies and organizations amidst the demand for reforms in work styles, new lifestyles, etc.
Examples of New Challenges in Cybersecurity
- Safe telework practices
We would like to review the measures necessary to protect confidential information accessed from outside the company and from terminals used outside the company. - Secure use of cloud services
We wish to address the risk of information breach arising from inappropriate use of cloud services (shadow IT) that the information systems department is unaware of. - Migration from VPN (Virtual Private Network)
The IP addresses of VPN devices are open to the outside world and thus vulnerable to attack; we wish to address security issues such as the vulnerability of the devices themselves, as well as issues concerning communication stability and scalability. - Unified security policies for headquarters, branch offices, overseas offices, etc.
We want to apply a unified policy to raise the level of security to a certain standard, which varies from location to location.
"Zero Trust" Model
Zero Trust (Zero Trust Network, Zero Trust Architecture), which, as the term implies, means "trust nothing," is a security concept in which any access to corporate resources, both inside and outside the network, is verified before being granted. Unlike the conventional model of defending at the boundary between the company's own network and the Internet (outside the company), the system allows operations to be conducted "securely" from anywhere at any time.
Steps to achieve Zero Trust Security
In implementing security measures based on the Zero Trust Model, we provide comprehensive support for clients' security measures - from sorting out current issues, proposing services and products necessary to solve them, to implementation and post-implementation operations.
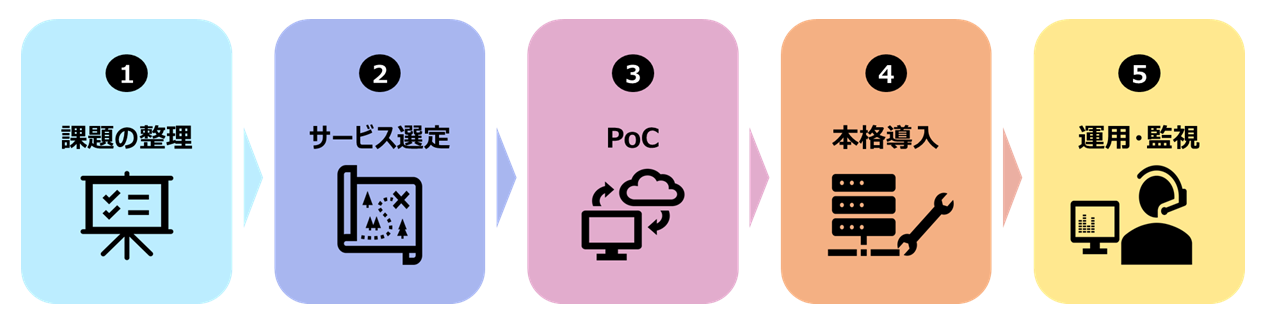
Organizing Issues
Service Selection
PoC
Full-scale implementation
Operation and Monitoring
Zero Trust Security Compliant Solutions
Three technical elements to achieve Zero Trust
The technical elements required to achieve the mechanism for providing security independent of device and user location is categorized into three perspectives.
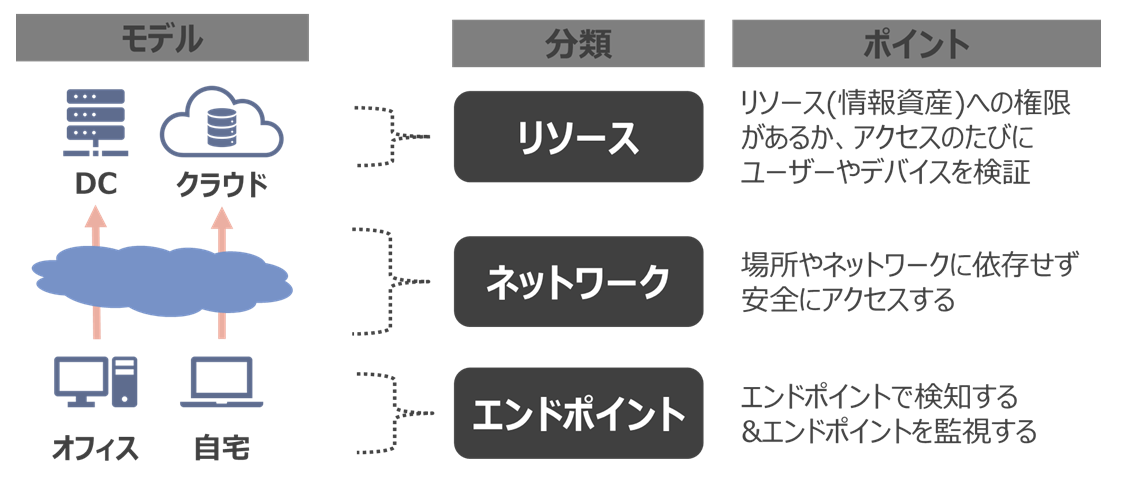
Solutions based on three technical elements
The three technical elements of resource, network, and endpoint and their compliant solutions are combined and applied according to client's requirements.
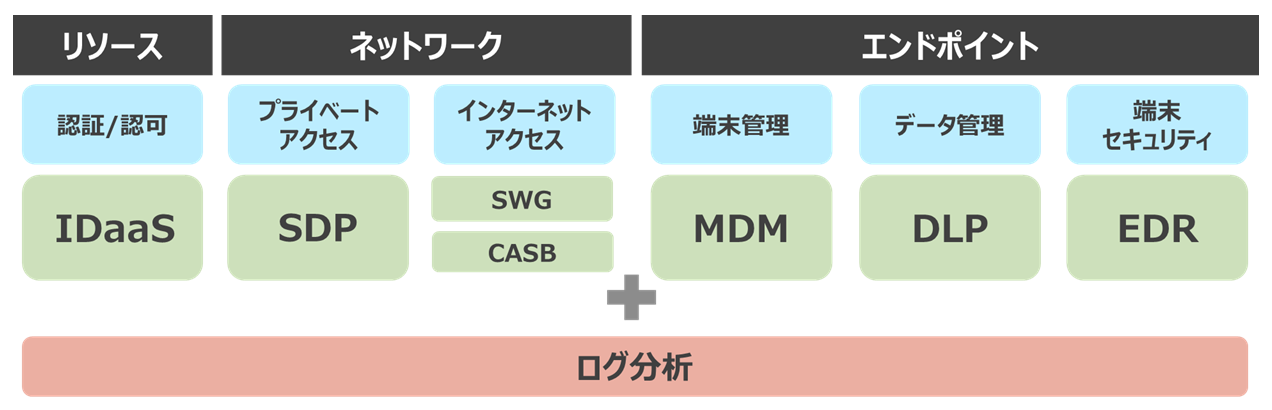
*Inquire separately to know whether certain products can be linked and how.
* "Compliant Solution" is an example. Contact us for inquiries concerning products other than those listed below.
-
■Compliant Solution
- Azure Active Directory (Azure AD)
https://www.microsoft.com/ja-jp/ (This will take you to Microsoft.com)
[Network] Private Access: SDP (Software Defined Perimeter)
■Compliant Solution
- Zscaler Internet Access/Zscaler Private Access
https://www.zscaler.jp/ (This will take you to the website of Zscaler)
[Network] Cloud Control: SWG (Secure Web Gateway)
■Compliant Solution
- Zscaler Internet Access/Zscaler Private Access
https://www.zscaler.jp/ (This will take you to the website of Zscaler)
[Network] Shadow IT Countermeasures: CASB (Cloud Access Security Broker)
■Compliant Solution
- McAfee MVISON Cloud
- Microsoft Cloud App Security
https://www.microsoft.com/ja-jp/ (This will take you to Microsoft.com) - Zscaler Internet Access/Zscaler Private Access
https://www.zscaler.jp/ (This will take you to the website of Zscaler)
[Endpoint] Mobile Device Management (MDM)
■Compliant Solution
[Endpoint] Data Management: DLP (Data Loss Prevention)
■Compliant Solution
- Contact us separately.
[Endpoint] Terminal Security: EDR (Endpoint Detection and Response)
■Compliant Solution
- Tanium Endpoint Management
https://www.intellilink.co.jp/business/security/tanium - Endpoint Monitoring Service with IntellilinkARGUS
*"Tanium Endpoint Management" - a 24/7 Monitoring and Operation service - Microsoft Defender ATP
https://www.microsoft.com/ja-jp/ (This will take you to Microsoft.com) - Cybereason EDR
https://www.cybereason.co.jp/ (This will take you to the website of Cybereason)
Log Analysis
■Compliant Solution
- Microsoft Azure Sentinel
https://www.microsoft.com/ja-jp/ (This will take you to Microsoft.com) - Exabeam, a user and equipment behavior analysis solution
https://www.intellilink.co.jp/business/security/exabeam - Threat Hunting Service
https://www.intellilink.co.jp/business/security/threat_hunting
*Threat Hunting involves investigating, analyzing and searching for any traces of threat intrusion based on the threat intelligence accumulated by receiving logs. We recommend using this service when conducting research and analysis on a spot basis.
Related Information
Columns/Article Contributions
[Mynavi News] Why Zero Trust Now?
Part 1: "What is Zero Trust Security?"
https://news.mynavi.jp/article/zerotrust-1/
Part 2: "Overview of Zero Trust"
https://news.mynavi.jp/article/zerotrust-2/
Part 3: "Solutions Required by Zero Trust - Part 1"
https://news.mynavi.jp/article/zerotrust-3/
Part 4: "Solutions Required by Zero Trust - Part 2"
https://news.mynavi.jp/article/zerotrust-4/
Part 5: "Introducing the Zero Trust Model"
https://news.mynavi.jp/article/zerotrust-5/
[@IT Publication] Special Feature: Integrating Security and Networks with "SASE" Using the Cloud (2)
Where and to What Extent Should Companies Aim for the Ideal of Zero Trust/SASE--Why NTT DATA INTELLILINK Introduced it Early
https://www.atmarkit.co.jp/ait/articles/2103/09/news003.html
Introductory Materials
Video
[Lecture Video] Thinking about Zero Trust Security - What we Found while Increasing the Remote Work Rate of Developers to 90% -
https://www.youtube.com/watch?v=02UTm3Gnt6k
* These products or services are only available in Japan.