The Japanese government's "Cybersecurity Strategy" recommends strengthening "Cyber Hygiene," which is the concept of reducing organizational risks through real-time monitoring of the security status of hardware/software within the organization, continuous management and elimination of vulnerabilities.
However, there is a large variety and volume of hardware/software to be managed, and the introduction of a good vulnerability management platform has become indispensable to effectively check the hardware/software for vulnerabilities that occur daily and apply security patches to address these vulnerabilities.
Overview
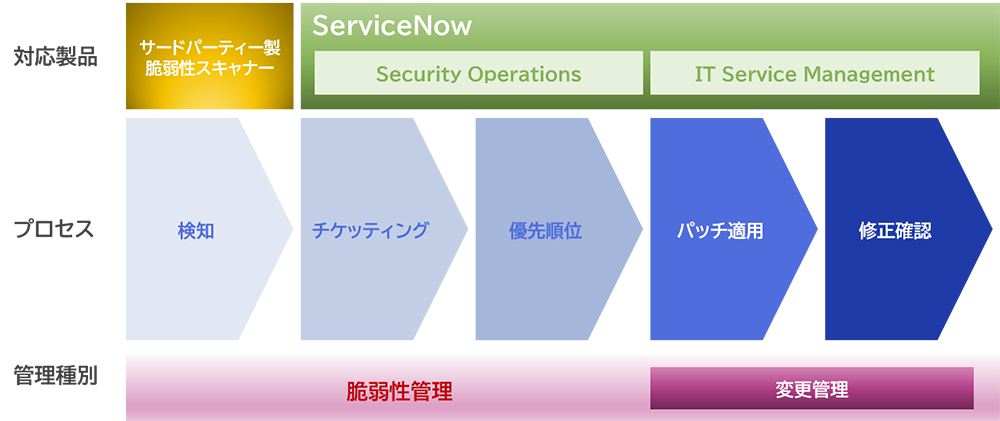
We offer a vulnerability management solution that combines ServiceNow Security Operations (SecOps) and third-party vulnerability scanners.
SecOps' workflow management around its high-performance configuration management database (CMDB) coupled with well-known third-party vulnerability scanners automates the entire process from vulnerability scanning to vulnerability response completion, enabling accurate and efficient vulnerability management with fewer members.
Strengths
Our vulnerability management solution has three key features—
1) Automated vulnerability management
2) Prioritization of patching
3) Assured vulnerability response
Vulnerability Management Process
The vulnerability management process combining ServiceNow and third-party vulnerability scanner is generally as follows:
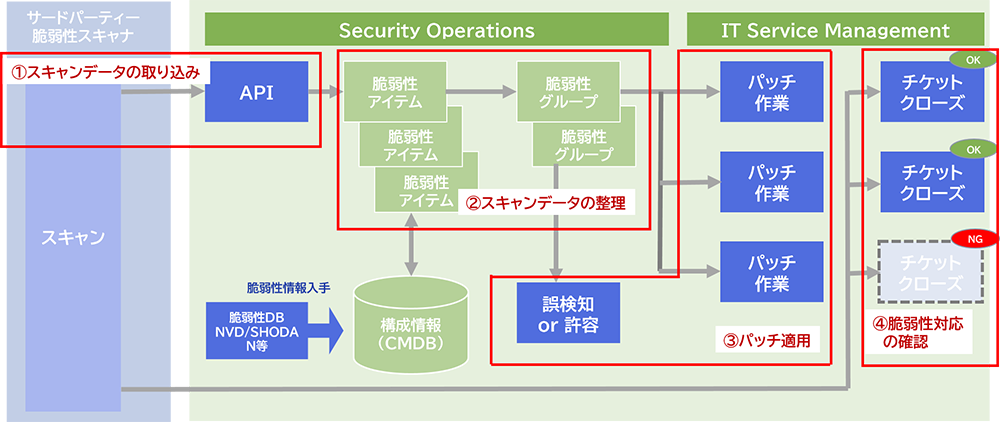
[1] Acquiring scan data
Identifying vulnerabilities in managed devices with a third-party vulnerability scanner.
Scan data is acquired by SecOps through the API.
[2] Organizing scanned data
The acquired scan data is matched with the configuration information in the configuration management database (CMDB) maintained by SecOps based on the IP address of the managed target, etc., to generate vulnerability items that are created by multiplying the configuration information with the vulnerability information. A vulnerability item is the smallest unit in vulnerability management.
Several vulnerability items are grouped together, and vulnerability management is implemented on a group-by-group basis.
Vulnerability groups are prioritized for patching based on a score calculated using logic taking into account the vulnerability risk score as well as organization-specific business impact.
[3] Patching
SecOps assigns a responding organization to each vulnerability group for patching work and sets a deadline for completion.
The assigned responding organizations must implement the patching by the deadline.
If these set patching deadlines are exceeded, these vulnerability groups are managed as exceptions through the approval flow if it is acceptable not to apply the patch or if it is a clear case of a false positive.
The patching process is managed using the change function of ServiceNow IT Service Management (ITSM), which is a separate product from SecOps.
[4] Confirmation of vulnerability response
When the patching process is complete, SecOps automatically instructs the vulnerability scanner to rescan to ensure that the patch has been applied correctly. If the same vulnerability is not found, the status is set to "closed" and the process is terminated; whereas, if the same vulnerability is found again, the status is restored to the original status and the process is restarted again.
Our Solution Service
In addition to selling licenses for third-party vulnerability scanners and ServiceNow products, our engineers with extensive experience in security technology and project management provide total support from design to implementation to operation in order to provide our customers with highly complete vulnerability management solutions.
Note: We only provide support for third-party vulnerability scanners recommended by us.
For Inquiries
* These products or services are only available in Japan.